Lesson 5: Packets
Widget
Overview
Students learn that large messages sent over the Internet are actually divided into individual packets and explore the challenges this creates. First students explore a version of the Internet Simulator that breaks messages into packets to get a sense for how it works. Students then use an activity guide that walks them through the challenges that dropped or out-of-order packets create. They then design their own protocol that addresses these challenges. At the end of the lesson students watch a video and learn and the User Datagram Protocol (UDP) and The Transmission Control Protocol (TCP), two different protocols for sending messages broken into packets.
Purpose
Information on the Internet is not sent all at once, but is instead broken into smaller chunks of data called packets. Each packet is sent through the Internet individually and may actually take different paths or arrive at different times than others. Once they arrive the receiver will use the packets to recreate the original file.
Two protocols used to send data as packets are UDP and TCP. The User Datagram Protocol (UDP) simply sends all the packets. If some arrive out of order or are entirely missing there's no system to fix the errors. The Transmission Control Protocol (TCP) numbers packets before sending them so that the receiver can correctly reorder the packets and request missing packets be resent.
Only one of these two protocols will be used, depending on the situation. TCP takes longer than UDP because of the error-checking done to guarantee every packet was received. TCP is used to send information like emails, images, websites, and more where saving fractions of a second is less important than accuracy. In instances like live-streaming television or online gaming where speed is most important, UDP will be used since it is faster and there's less benefit to correcting errors.
This lesson gives students a hands-on experience with the ideas behind both protocols and helps them understand the implications of splitting large files into packets when sending them online.
Note: UDP is not covered in the video at the end of the lesson.
Agenda
Lesson Modifications
Warm Up (5 mins)
Activity (30 mins)
Wrap Up (10 mins)
View on Code Studio
Objectives
Students will be able to:
- Describe how information flows through the Internet as a datastream of packets
- Explain how packet numbering and re-ordering can allow for large messages to reliably be sent even if packets are dropped or arrive out of order
- Explain the differences between the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP)
Preparation
- You can test out versions of the Internet Simulator by opening it in two tabs and communicating with yourself. Briefly try out the activity in the activity guide, including sending the messages and reading the logs, to understand what students will see.
- Preview The Internet: Packets, Routing, and Reliability - Video.
- The previous lesson's Teacher Guide - Routers & Redundancy - Unit 2 Lesson 4 - Activity Guide contains helpful tips on setting up routers and managing student conversations.
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
- CSP Unit 2 - The Internet - Presentation
For the Students
- U2L05 Packets - Activity Guide
- The Internet: Packets, Routing, and Reliability - Video (download)
Teaching Guide
Lesson Modifications
 Attention, teachers! If you are teaching virtually or in a socially-distanced classroom, please read the full lesson plan below, then click here to access the modifications.
Attention, teachers! If you are teaching virtually or in a socially-distanced classroom, please read the full lesson plan below, then click here to access the modifications.
Warm Up (5 mins)
Discussion Goal
Goals: This prompt foreshadows the challenge students will see in today's lesson and also the core difference between the two protocols they'll look at, TCP, and UDP. You don't need to cover either of those at this point in the lesson. Some key points to draw out:
- In the first instance you would probably just load them into boxes and carry them over. You might even be ok if some were lost or the order got messed up. What matters is speed.
- In the second case there'd need to be some kind of record keeping to make sure that every book was recorded as well as the order it was placed in.
- In both cases you wouldn't move the entire library at once, you would move boxes or chunks of books at a time.
Note this is a tight lesson with a significant wrap up. Aim to keep this warm up short and move to the main activity quickly.
Prompt: Suppose our school library is moving to a new building on campus and the librarian has asked for your help.
- What approach would you take if you just needed to clear out the space by the end of the day?
- How would your approach change if you had more time and wanted to check that every book made it safely and was on the same shelf it was on before the move?
Remarks
In the last lesson we learned that messages can take different paths to get to the same place on the Internet. Sometimes, we need to send really large messages over the internet, like movies or large pictures. Just like moving your entire school library, there are problems that arise when we want to send large messages on the internet. Today we're going to learn about two different protocols for sending information online, one that's used when all we care about is speed, and one that's used when accuracy is more important.
Activity (30 mins)
New Version of the Internet Simulator (5 mins)
Do This: Direct students to level 2 of the lesson on Code Studio.
Group: Place students in pairs. Each student should log into the Internet Simulator.
Prompt: Follow the steps below to get familiar with this new version of the Internet Simulator.
- Join a different router than your partner
- Ask your partner for their IP address.
- Using only the simulator, have a conversation about one of these topics: Your favorite movie, Your favorite band/artist, The one superpower you wish you had
- Try to discover every way the simulator is different than last time.
Circulate: Look for students to notice that messages are being cut off after 80 bits. Once several students notice this, ask one of them to share with the class.
Teaching Tip
Why 80 bits?: The choice to make the messages 80 bits long is totally arbitrary to motivate the lesson. IP packets are much larger. This limit makes it easier for students to quickly run into the core challenges of this lesson.
Previewing Metadata: While you will formally cover this vocabulary in the wrap up, use this moment to start using this term so it will be more familiar later.
Discuss: Briefly discuss as a class the changes they've seen in the Internet Simulator. The main things they should notice are
- A single message can be made up of many “packets” which you can add with the “Add Packet” button
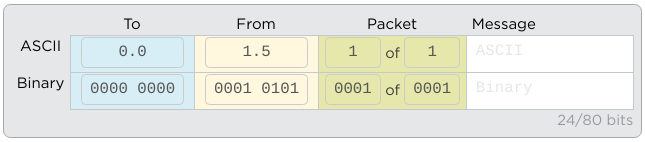
- Packets can only be 80 bits long. 16 bits are already used for packet metadata, data added to help route the messages. You only have 64 bits, or 8 ASCII characters free for each of your messages
- When you send the message, all packets appear to be sent at once, but may arrive out of order.
Activity Guide - Packets - (25 mins)
Distribute: U2L05 Packets - Activity Guide
Why Packets: Read the paragraph explaining why messages are divided into packets.
Protocol 1 - Just Send All the Packets: Guide students through creating a single multi-packet message to send to their partner. They should aim for roughly 5 - 10 packets to increase the likelihood of some packets dropping or arriving out of order.
Read the Traffic: Instruct students to read the router logs so they can watch their messages travel through the network. They should then answer the two questions provided. Students may need help narrowing down the logs to just their traffic. If they find their packets are taking the same route or none or dropping then make sure they're connected to different routers. They may also just get lucky and need to send a second message.
Discuss: Briefly discuss responses to the U2L05 Packets - Activity Guide. Have a few different groups share out. See if you can find the examples students share in the router logs and display them at the front of the class. Focus on the following points:
- Packets can take different paths from one another, just like messages
- Packets can be dropped, just like messages in the previous lesson
- As a result, messages may arrive out of order or incomplete
- While a human might be able to understand the original message based on context, a computer would not, the message would simply be lost
Teaching Tip
Encouraging Good Protocols: If students are unsure of how to write their protocols, try asking some of these questions:
- Think back to the warm up. How would you label the moving boxes for the library?
- Could you use a similar labeling system for the parts of your message?
- Since we have limited space to work with for each message, what short codes could you use to label them? (Numbers, letters)
- What signal can we send to let the receiver know how many messages to expect in total?
- What signal can we send to let the sender know to resend a particular message?
- What signal can we send to let the sender know we received all the messages?
More Than One Solution: There's lots of ways to solve this problem! Emphasize to students that while their protocol needs to solve the problem, there's not just one right answer and their solution doesn't need to look like their classmates.
Looking Ahead: In the future version of the Internet Simulator students will see that packets are actually typically numbered like the image below. You don't need to share this information but it is useful to know where the Internet Simulator is heading.
Remarks
Protocol 1 has some issues as we just saw. Packets can arrive out of order or totally get lost and there's no way for the computer to tell what happened. That said, it's a really simple protocol, and it's fast. In the real world, this is known as UDP or User Datagram Protocol.
Let's go over this in more detail.
Do This: Click through the animation and read through the main idea, basics of how it works, and the use in real life.
Remarks
Now let's see if we can develop a protocol that gives us better accuracy if we're ok taking some more time.
Protocol 2 - Check for Errors - 10 mins: Give students 10 minutes to develop a protocol that can address the challenges they just saw. Just as before students should construct a multi-packet message and send them all at once. After that initial message, however, the receiver and sender can continue to communicate to ensure the full message is received and correctly ordered. Circulate the room checking in on different groups and encouraging them to test their protocols out and be ready to share their solutions with the class.
Share Protocols - 5 mins Give two or three groups a chance to share their solutions with the class, either by describing it out loud or showing it on a projector at the front of the room. As a class discuss some of the shared features in their protocols. If short on time you may just ask students to raise their hands if their protocols included one of the features below.
- Each packet is numbered or otherwise indicates which order it should go in
- Each packet includes the total number of packets, again perhaps with a number, so the receiver knows how many packets to expect
- The receiver requests missing packets or confirms received packets so the sender knows which to resend
- The sender and receiver both know when the message has been successfully received
Remarks
We just developed a protocol that in the real world is known as TCP or Transmission Control Protocol. Let's take a look at more of the details.
Do This: Click through the animation and read through the main idea, basics of how it works, and the use in real life.
Wrap Up (10 mins)
Teaching Tip
Key Video Takeaways: The video includes a lot of information about how packets move through the Internet. The most important points for students to understand are that
- Large files are split into packets to be sent
- Packets may take different routes through the network and arrive out of order
- TCP ensures that packets that arrive out of order or are lost are re-ordered
- Packets include metadata like their IP address or a packet number to help move them through the network or reorganize them when they arrive
- Collectively this system makes the Internet more reliable
Covering UDP: UDP is not covered in the video and students do not need to understand it in great detail. The depth of explanation in the slides is sufficient to explain the differences between them and why each would be used.
Remarks
The first protocol we looked (UDP) at was simple, but it had some problems. The second protocol we just invented (TCP) is much more accurate, but it takes longer. Depending on the situation, websites will choose the protocol that makes sense. Let's watch a video that teaches us more about how packets really work on the Internet with TCP.
Display: Watch The Internet: Packets, Routing, and Reliability - Video
Journal: Have students add the vocabulary words: Datastream, Packet, Packet Metadata, Transmission Control Protocol (TCP), and User Datagram Protocol (UDP)
Assessment: Check For Understanding
Check For Understanding Question(s) and solutions can be found in each lesson on Code Studio. These questions can be used for an exit ticket.
Question: Which of the following is true regarding the way information is transmitted on the Internet?
Question: Terminology matching
- Lesson Overview
- Student Overview
Student Instructions
Student Instructions
In 50 words or less, describe the concept of a number system.
Why are rules required for a number system to be useful?
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2017)
NI - Networks & the Internet
- 2-NI-04 - Model the role of protocols in transmitting data across networks and the Internet.
- 3A-NI-04 - Evaluate the scalability and reliability of networks, by describing the relationship between routers, switches, servers, topology, and addressing.
- 3B-NI-03 - Describe the issues that impact network functionality (e.g., bandwidth, load, delay, topology).
CSP2021
CSN-1 - Computer systems and networks facilitate how data is transferred
CSN-1.B - Explain how the Internet works.
- CSN-1.B.5 - Routing on the Internet is usually dynamic; it is not specified in advance.
- CSN-1.B.6 - The scalability of a system is the capacity for the system to change in size and scale to meet new demands.
CSN-1.C - Explain how data is sent through the Internet via packets.
- CSN-1.C.1 - Information is passed through the Internet as a data stream. Data streams contain chunks of data, which are encapsulated in packets.
- CSN-1.C.2 - Packets contain a chunk of data and metadata used for routing the packet between the origin and the destination on the Internet, as well as for data reassembly.
- CSN-1.C.3 - Packets may arrive at the destination in order, out of order, or not at all.
- CSN-1.C.4 - IP, TCP, and UDP are common protocols used on the Internet.
