Lesson 10: Protecting Data Part 2
Overview
This lesson is a guided tour of multifactor authentication and software updates that students can use to protect their data. Following these discussions, students are introduced to a stimulus question where they will apply their knowledge gained throughout the unit to answer questions about an innovations data, benefits and harms, effects, and security or privacy concerns.
Purpose
This lesson serves two purposes. The first is to provide the final pieces of content students need to know in this unit - related to multifactor authentication and virus scanning software. These are tools students can use to protect the data. The second purpose of this lesson is to introduce students to questions that follow the same format as the questions students will encounter on the AP Multiple Choice Exam. The specific types of questions students will see in this lesson will help prepare them to answer "Single-Select Questions with Reading Passage", or SSQRP. These types of questions show up on the AP Computer Science Principles Multiple Choice Exam and involve a series of questions about a fictitious computing innovation.
Agenda
Lesson Modifications
Warm Up (5 mins)
Activity (35 mins)
Wrap Up (5 mins)
View on Code Studio
Objectives
Students will be able to:
- Explain the benefits of multifactor authentication
- Discuss the benefits of computer virus scanning software and the need for regular updates
- Thoughtfully answer a stimulus question
Preparation
- Preview the slides
- Read through the stimulus question
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
- CSP Unit 10 - Cybersecurity and Global Impacts - Presentation
For the Students
- Call Center - Reading Passage - Resource
Teaching Guide
Lesson Modifications
 Attention, teachers! If you are teaching virtually or in a socially-distanced classroom, please read the full lesson plan below, then click here to access the modifications.
Attention, teachers! If you are teaching virtually or in a socially-distanced classroom, please read the full lesson plan below, then click here to access the modifications.
Warm Up (5 mins)
Remarks
In the previous lesson we discussed how your data is protected through encryption. Today we are going to focus on what you can personally do to keep your data protected.
Discussion Goal
Students should discuss good password management, building off of their knowledge from earlier in the unit. The following slide contains best practices, but your students may have some more concrete suggestions for how they craft complex but memorable passwords.
Prompt: What strategies do you use when creating a good password?
- Note: Make sure students don't reveal any of their current passwords in the discussion!
Remarks
A good password is easy to remember, but hard for someone else to guess based on knowledge they have about you.
If your password is your dog's name and your birthdate, that's all personal information that someone else might be able to guess!
Activity (35 mins)
Protecting Data (15 mins)
Display: Use the activity slides for this lesson to guide the discussion on Protecting Data
| Slides | Speaker Notes |
|---|---|
 |
Say: There are things you can do to protect your data. The first one we are going to talk about is multifactor authentication. |
 |
Say: When we discussed passwords in the Warm Up, this was an example of single factor authentication. There is one layer of protection, that is centered around something you know: your password.  Click through animation Click through animation |
 |
Say: Two factor authentication adds another layer. Prompt What do you think is another way of protecting your data?  Click through animation Click through animation Say: In addition to something you know, another layer is something you possess like a phone. Have you ever been required to put a phone number in when getting a password authenticated? Sometimes a text will be sent to your phone with a code to enter in, proving that you are the person who has the phone. This layer means someone who just guesses your password can't get in to your account - they would also need access to your phone. |
 |
Prompt: What are the problems with this system? How could it be hacked? Goal: Guide the discussion towards the answer that a phone could be stolen or a sim card lost. |
 |
Prompt: There's another layer that can be used to protect your data. Can anyone guess what it is?  Click through animation Click through animation Say: If you guessed something physical or perhaps "biometrics", you are correct!  Click through animation Click through animation A fingerprint is an example of this. A retina scan of your eye is another example. These three options: something you know, something you possess, and something you are make up multifactor authentication, which involves at least two of these options and preferably all three. If someone tried to access your account, they would be required to know your password, have access to your phone and your fingerprint! |
 |
Prompt: Why is this better than Single Factor Authentication? What are the challenges with the system? Is it worth any of the risks? Note: Allow students time to think through these prompts, perhaps in small groups before having a whole class discussion. Multifactor authentication can keep data more protected than single factor authentication, but it requires extra steps which add time and often money (the cost of a phone, etc.). There are also privacy concerns with having your fingerprints or retina scanned. |
 |
Say: Another way to protect your data involves updating your software. |
 |
Say: Let's review. What is a virus? Note: Give students an opportunity to glance through the notes and review computer viruses from lesson 7. |
 |
Say: Do you remember how to protect your device from a computer virus? Note: Allow students to suggest different forms of protection before clicking through the animation.  Click through animation Click through animation Say: Two things you can do: use virus scanning software and update system software. You could also say, keep all software updated! |
 |
Say: Data protection is a moving target. It's not a one and done process. It's not enough to install virus protection software and never thing about it again! New viruses and threats are constantly being developed - you need to keep your software up to date and use the best authentication practices you can in order to keep your data safe! |
Single-Select Questions with Reading Passage (SSQRP) (20 mins)
Remarks
Now we are going to shift gears and discuss Single-Select Questions with Reading Passage or SSQRP. What is SSQRP?
Over the course of this unit you've learned a lot about computing innovations. SSQRP is designed to assess how well you understand the various issues surrounding computing innovations. The good news is, you aren't expected to have any prior knowledge about the computing innovations discussed in these questions - they are all made up. You will have a short reading passage followed by five multiple choice quesions that focus on data, purpose and effect, benefits and harms, and security concerns. SSQRP is present on the AP CSP exam, and there will be two in the end of unit assessment.
Distribute: Hand out Call Center - Reading Passage - Resource
Do This: Direct students to take a few minutes to read the information about the computing innovation. They do not need to memorize anything - they can look back at the paper at any time while answering the questions.
Do This: Read through the "Sample Questions" slide as a class. This slide introduces the two categories from which questions will be pulled, along with common phrases. Go through the phrases, and make sure students understand what each phrase means. For example, you may want to spend time on the phrase "unintended effect" as this may be a confusing combination of words for some students. The focus here is on understanding question types - it may be useful to have students think through what some of the possible answer options might be for some of the questions.
Teaching Tip
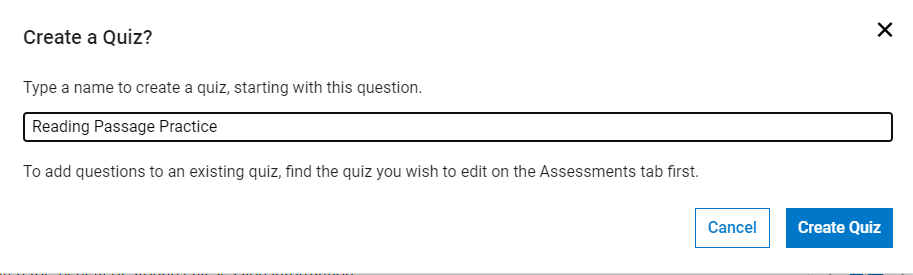
To assign questions to students on AP Classroom, once logged in navigate to the Question Bank. Search for the following question:
benefit of storing call session information

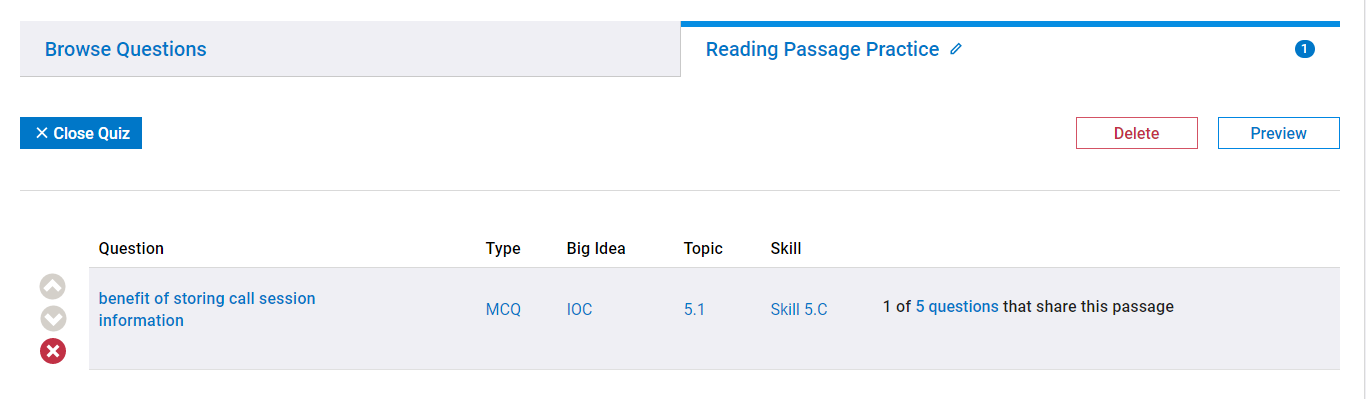
Then add this question to a quiz like so:
Once you have added one question, you'll see that you can easily import the other 4 practice questions into your quiz.
Click where it says "5 questions"
And choose to add all of the questions.
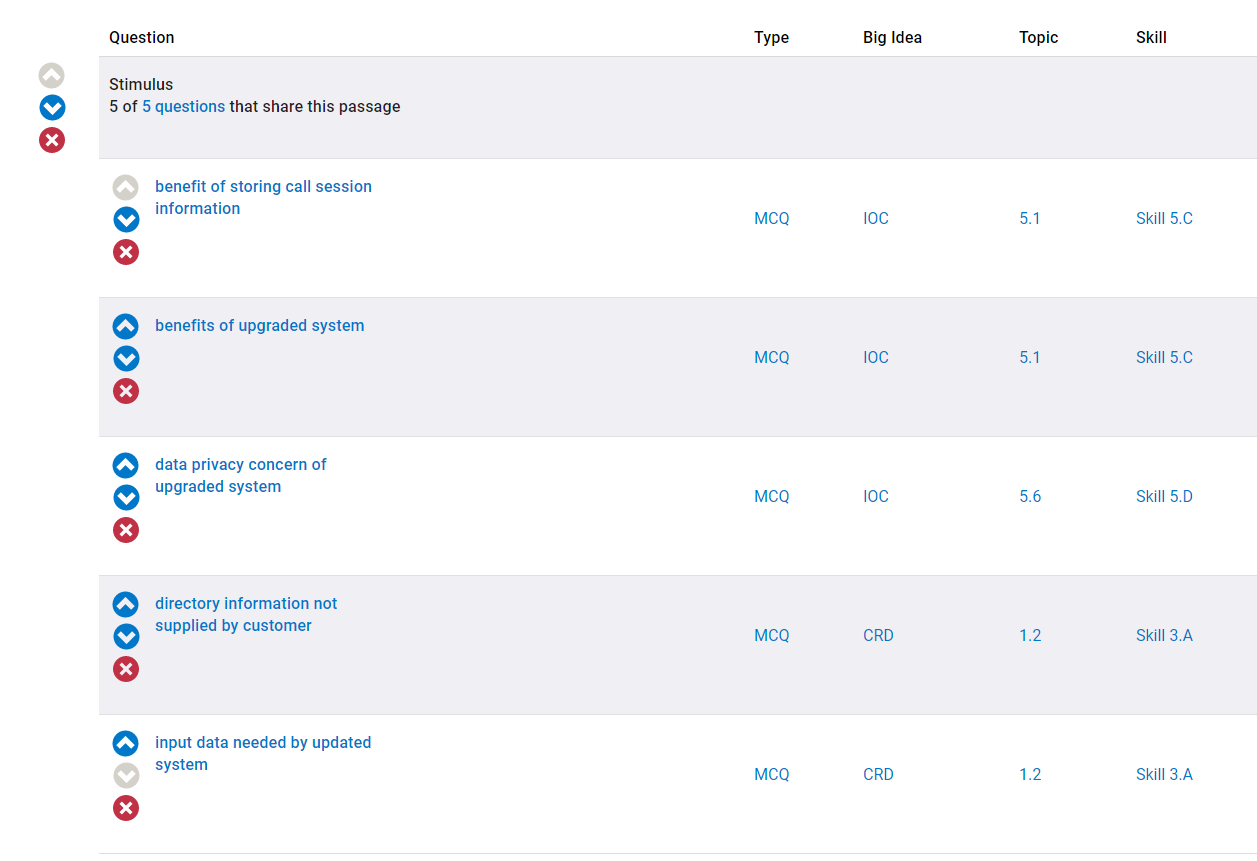
Following this, you can assign the assessment to your students and they can practice the Reading Passage questions.
AP Classroom: Direct students to navigate to AP Classroom and complete the five practice questions relating to the Call Center. Allow students to see the answers. Following this, discuss with the class any confusion over the questions or the computing innovation.
Remarks
And that's SSQRP! Hopefully you saw through this example the steps of reasoning through the answers and applying your knowledge of the issues related to computing innovations.
Wrap Up (5 mins)
Remarks
In the first half of class, we discussed protecting data. Let's review that.
Discussion Goal
If students are struggling with answering this question, prompt them with more specific questions:
- How will you decide on your next password?
- Will you use two-factor or multifactor authentication when you have the opportunity?
- How often do you update your software?
- How up to date is the software on your devices?
Prompt: Discuss with a partner how you plan to protect your data.
Journal: Students add to their journals the definitions for: multifactor authentication and computer virus scanning software.
Assessment: Check For Understanding
Check For Understanding Question(s) and solutions can be found in each lesson on Code Studio. These questions can be used for an exit ticket.
Question: Reflection: What concerns do you have about multifactor authentication? Is it a good long term solution for data privacy?
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2017)
NI - Networks & the Internet
- 3A-NI-06 - Recommend security measures to address various scenarios based on factors such as efficiency, feasibility, and ethical impacts.
- 3A-NI-07 - Compare various security measures, considering tradeoffs between the usability and security of a computer system.
- 3B-NI-04 - Compare ways software developers protect devices and information from unauthorized access.
CSP2021
IOC-2 - The use of computing innovations may involve risks to your personal safety and identity
IOC-2.B - Explain how computing resources can be protected and can be misused.
- IOC-2.B.1 - Authentication measures protect devices and information from unauthorized access. Examples of authentication measures include strong passwords and multifactor authentication.
- IOC-2.B.10 - All real-world systems have errors or design flaws that can be exploited to compromise them. Regular software updates help fix errors that could compromise a computing system.
- IOC-2.B.11 - Users can control the permissions programs have for collecting user information. Users should review the permission settings of programs to protect their privacy.
- IOC-2.B.2 - A strong password is something that is easy for a user to remember but would be difficult for someone else to guess based on knowledge of that user.
- IOC-2.B.3 - Multifactor authentication is a method of computer access control in which a user is only granted access after successfully presenting several separate pieces of evidence to an authentication mechanism, typically in at least two of the following categorie
- IOC-2.B.4 - Multifactor authentication requires at least two steps to unlock protected information; each step adds a new layer of security that must be broken to gain unauthorized access.
