Lesson 9: The Need for Addressing
Overview
In this lesson, students explore more deeply how communication between multiple computers can work over the Internet. They do this by playing a simplified game of Battleship, in which the first game is played unplugged, in their table groups, and the second game is played using the Internet Simulator, so that multiple students can connect to each other and see each other’s messages. Students must devise a messaging protocol that makes it clear who is sending the message and who the intended recipient is.
Students then devise a binary protocol for playing this game which will entail developing an addressing system for players, as a well as a formal packet structure for transmitting data about the state of the game.
NOTE: this is a large lesson that will likely need to span 2 days of class.
Purpose
This lesson builds up to students learning about the “Internet Protocol” addressing system, commonly known as IP Addresses.
Up to this point in the course, the Internet Simulator has only assumed point-to-point communication. The "protocols" students were inventing mostly had to do with encoding information in binary, rather than also encoding communication information required for successful delivery of the message.
The lesson mimics a real problem that designers of the internet had to solve. Many computers are connected together by networks. So if a computer sends some bits out, those bits pass through many computers. How does a computer know who those bits are for? If a response is necessary, how does it send it back? This is a complicated question, but the first part of the answer is that you need an addressing system, and some kind of fixed structure for messages that everyone agrees on (a protocol) so messages can be interpreted properly. (We'll get to routing later).
The Internet Simulator for this lesson is setup to “broadcast” every message to every person in the group. Since everyone receives any bits that were sent by anyone else, a method for identifying the intended sender and receiver of the message is needed. Students will invent a protocol for addressing messages.
Many network systems, such as local ethernet and WiFi, rely on addressing schemes to make sure bits are received by the correct computer based on address and for other computers to simply ignore messages not intended for them.
Agenda
Getting Started (20 mins)
Activity: Silent Broadcast Battleship (25 mins)
Activity 2: Invent a Binary Protocol for Battleship (20 mins)
Wrap-up
Assessment
Extended Learning
View on Code Studio
Objectives
Students will be able to:
- Explain why messages need to contain addressing information (sender/recipient identification).
- Invent an informal addressing protocol for use in the Battleship game.
- Recall that browsing the Internet entails computers sending each other requests and sending back data to satisfy those requests.
Preparation
- Copies of the Battleship game board for each student
- Poster paper or methods/materials for students to present
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
- U2L02 - Teaching Tips & Tricks Video - Video (download)
- Video Guide KEY for "IP Addresses and DNS" - Answer Key
For the Students
- Broadcast Battleship Game Board - Activity Guide
- Broadcast Battleship Rules - Activity Guide
- Internet Simulator - Part 3 - Video (download)
- IP and DNS Video Worksheet (Optional) - Video Worksheet
- Invent a Binary Protocol for Battleship - Activity Guide
- The Internet: IP Addresses and DNS - Video (download)
Vocabulary
- IP Address - A number assigned to any item that is connected to the Internet.
- Packets - Small chunks of information that have been carefully formed from larger chunks of information.
- Protocol - A set of rules governing the exchange or transmission of data between devices.
Teaching Guide
Getting Started (20 mins)
Teaching Tip
How to demonstrate the rules of Battleship
Not every student may have played Battleship before and even if they have, this mini-version of the game is different from the real thing. You should consider how you want students to learn the new rules and play with pencil and paper rather than the typical peg board. In the resources above there is a printable copy of the Broadcast Battleship Rules - Activity Guide, but there are alternatives to simply distributing those rules.
One possibility: Demo two player version in large format.
- Draw a large version of the battleship grids from the activity guide on two pieces of chart paper or on the blackboard where everyone can see.
- Nominate two students to stand back to back (so each student cannot see what the other is marking) to mark up the grids following your instructions - they will each place one ship that is two boxed in size, and then try to location and sink the other student's ship.
- Once people the get the gist of playing this paper and pencil version of battleship, ask "okay, what if we added a 3rd person so that each person was playing against two others simultaneously?
- Then have the students get into the actual activity and figure out the rest in their group of three.
Other possibilities:
- Project the rules on a screen at the front of the room
- Have students read/review a digital copy of the rules
- Have students play the game for "homework" - some free online versions of the game exist.
- Ask a student who knows the rules to explain. Who has played Battleship? How does the game work? What’s the object of the game? What are the rules?
Remarks
So far we have only solved Internet problems when you are connected to one other person (so-called "point-to-point" communication). Obviously, the Internet is bigger than that, and today we're going to look at problems that involve multiple people.
Introduce "Broadcast Battleship"
- We will start by playing a game that simulates some issues that arise when constructing the internet.
- We will play a crazy game of Battleship where instead of playing against one other person you will play multiple games against multiple other people simultaneously -- We call this "Broadcast Battleship"
- In our version today, you will play in groups of 3 (4 is OK)
- To make it easier to track, we've also simplified the playing board to just a 3x3 grid (instead of the classic 10x10)
- And we'll just play with paper and pencil.
Activity Goal
Why Battleship?
Teachers may want to substitute other games for battleship in this activity for a variety of reasons. However, if you do that be aware that battleship was chosen because it has several properties that force concepts of internet protocols to come out. Battleship has a relatively fixed size message length, a need to encode several different pieces of information (coordinates), to and from addressing, and a verification message (hit or miss).
Example Game Board
Below is an example game board included in Broadcast Battleship Rules - Activity Guide (click to enlarge)
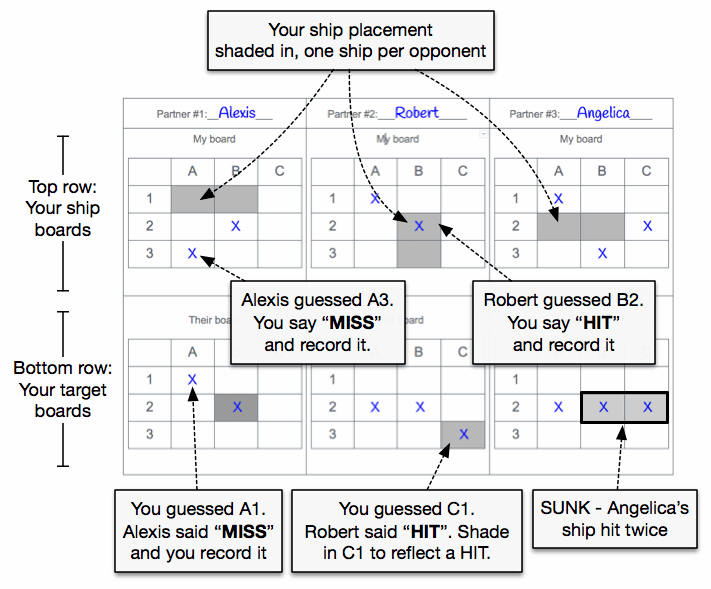
Battleship Setup
- Arrange students in table groups of 3. (A group of 4 is OK, but not recommended.)
- (Optional) Distribute Broadcast Battleship Rules - Activity Guide to each student.
- Distribute Broadcast Battleship Game Board - Activity Guide to each student.
- Review the rules for the multi-player version, and answer any logistical questions.
Play Broadcast Battleship - Round 1 - unplugged
-
Start Game Unplugged.
-
Give students a couple minutes to play the game.
-
Students might not finish the game, but students should get a good feel for how the game works and what the mechanics of the game are.
-
Pause the Game After 5 minutes
- After a couple minutes interrupt the game
- Assure students they'll return to playing in a minute
- they record their current spot in the game if necessary to pick up where they left off
Transitional Comment
- It seems that most of you have figured out a way to play battleship with your group.
- You will get to continue to play your game in a few minutes.
- We are going to add a new challenge: Your team is going to have to play Battleship without talking.
- You will only be able to use the Internet Simulator to communicate
Activity: Silent Broadcast Battleship (25 mins)
Teaching Tip
The first time students visit Code Studio for this lesson a tutorial video will pop up to shows how this works.
You may want to do one of the following:
- show this video to the whole class
- have students watch it individually
- have students skip the video and demonstrate the behavior to everyone
Introduce new version of Internet Simulator (Broadcast)
Transition to the Internet Simulator found in Code Studio for this lesson
- Students log in to Code Studio, and navigate to the lesson: “The Need for Addressing”
Highlight the differences in the new version:
- You connect to a “Room” with other people, instead of an individual partner.
- Every message that is sent gets broadcast to everyone in the "room", including you!
Teaching Tip
- You will probably need to enforce the NO TALKING rule
- Without talking, communication protocols will organically come out as students try to play the game in this new mode of the Internet Simulator.
- Assure students that they will get a chance to talk and collaborate before trying again.
Continue the game on the Internet Simulator
- Give students 5-10 minutes to finish their game using the Internet Simulator.
- Enforce the no-talking rule
- Students should quickly discover that they need to “address” their messages.
- That is, they need to indicate the sender (themselves) and the intended recipient somewhere in the message, in order for the game to work.
- Different tables (and different player pairs) may invent different ways of doing this. Some examples:
- “Hi, Tom, it’s Mary.”
- “Mary to Tom.”
- “Mary → Tom”
- “To Tom, From Mary”
- “Mary is asking Tom right now”, etc.
Some methods may be more informal, or buried in content of the message:
- “Tom, B4. This is Mary, by the way.”
- “That B4 message was for Tom. It’s Mary.”
- “I just sent that message. This is Tom. No, the other message.”
Teaching Tip
At this point, playing the game is less important than moving towards developing a clear and efficient protocol.
Students might notice that a concise protocol makes it harder for them as humans to play the game, but remind them that they are the computers in this activity.
Why would it be important to keep the message short and standardized? Make a connection to the protocols from previous lessons: Sending Numbers and Sending Text.
Refine and Reflect.
After the 5-10 minutes allow groups to talk. They should discuss standardizing their protocol for sending messages. They should consider:
- What protocol have they been using? Did they have a protocol at all?
- How can they standardize their communication?
- How do they make their message as clear as possible?
- How do they make their message as efficient (short/easy to interpret) as possible?
Play Game. Round 2.
After groups have had a chance to coordinate and refine their protocols, give them a chance to try it out on a fresh game.
- Have students return to the Internet Simulator, start a new game and test out their protocol.
- Remind them of the No Talking rule.
- If necessary, distribute a clean copy of Broadcast Battleship Game Board - Activity Guide for use in this round.
After 5 minutes or enough time to try out their new protocol, transition to the next activity.
(Optional) Individual Reflection
-
Before moving on to the group whip around, have students complete the reflection question in Code Studio or in their journal:
- How did your group decide upon a system for sending messages in the Battleship simulator?
- Were there disagreements or problems?
- How were they resolved?
Activity 2: Invent a Binary Protocol for Battleship (20 mins)
Teaching Tip
If students are having difficult getting started:
- The activity guide contains a number of suggestions and questions to get thinking started -- Start by lead students through these questions
- Use the exemplar solution as a guide to coerce students into thinking about at least some element of that to get un-stuck.
Here a few other prompts you can use
- How will you standardize the recipient and sender addresses?
- Should you encode people's names or (hint) use a number?
- How would a recipient of your message know where address ends and the other begins?
- What other information do you need to include?
Distribute and go over Invent a Binary Protocol for Battleship - Activity Guide
(From the Activity Guide)
Overview
Previously you came up with a method for exchanging messages on an open broadcast channel to play multiple games of Battleship at once. Now that you’ve played Battleship this way, with your group or with a partner, describe an efficient binary protocol for playing a 3-person game of Battleship that can be played accurately over the Internet Simulator.
Let “efficient” mean that your protocol uses the smallest reasonable number of bits (0s and 1s) to make messages for Battleship that still contain all of the necessary information for playing the game.
Give groups about 10 minutes to work
- Use the teaching tips to help students along if they struggle to start.
Discussion Goal
A good solution uses a numeric address (not tied to a person’s name) and a fixed length message. The number allows you to uniquely identify players (like a phone number) and having a fixed length helps know where each "chunk" of the message starts and ends.
How many bits do you need for addresses? -- For 3-person Battleship, you only need 2 bits for an address, since there are only 3 people; each can have a unique code.
How many bits are needed for the total message? -- Answers to this will vary and creativity should be encouraged. However, it should be evident from the students’ protocols that they recognize the fundamental elements of the game and what might be able to be compressed into only a few bits.
(See the example solution).
Discuss & Share
After groups have had some time to work bring the class together.
- Ask if any group would like to share their protocol
After the group has presented open up the discussion to draw out similarities and differences. Here are a few prompts:
- "Did any other group do something similar? or something completely different?"
- "What pieces of information were common across all of the protocols? Sender, recipient, cell number, hit/miss info."
- "If we were to play a different game, what data would stay the same? What would change?"
Use this question to transition to the wrap-up:
What do you think all of this has to do with the Internet?
(Optional) Exemplar Solution
You may choose to share this with your students or not. You might just use this exemplar as background knowledge to help you guide students' solutions.
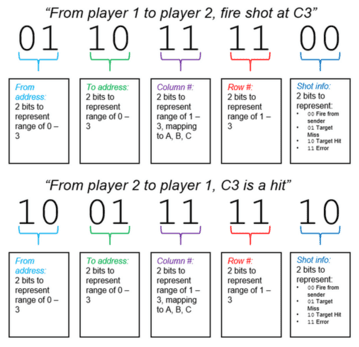
A simple, but clever encoding protocol is to recognize that the addresses, coordinates, and hit/miss messages can each be encoded with 2 bits (i.e. a list of 5 numbers in the range 0-3), and that you can make a combined message protocol that would allow a player to communicate anything needed for the game.
The scheme shown below uses 10 bits total. The last two bits are interesting: they indicate whether this is a shot being fired for the given row and column or whether it’s a hit/miss response to the given row and column. Since the respondent who says hit or miss must verify the coordinates of the shot they are responding to, the recipient doesn’t have to remember the last shot they called.
Wrap-up
Real IP Addresses - Background and Video.
It turns out computers on the Internet are addressed in a similar way to phones for many of the same reasons. The real addresses used on the Internet are called “Internet Protocol Addresses” or IP Addresses for short.
Teaching Tip
Do some rapid research (Optional)
At this point, you could have students look up the real IP packet structure and it might make some sense to them. They might find it satisfying and empowering to be able to understand a more technical article. The Wikipedia article on IPv4 packets shows how all the bits are laid out: https://en.wikipedia.org/wiki/IPv4#Packet_structure
However, we have not yet covered a major aspect of packets, and the real need for their existence, which is that they are used to breakdown very large messages into smaller chunks to improve reliability of transmission. We cover packets in a future lesson.
Video: The Internet: IP Addresses and DNS - Video
- Have students watch the video (display for all, or have students watch in Code Studio - it's the level after the Internet Simulator)
-
Have students complete IP and DNS Video Worksheet (Optional) - Video Worksheet
-
You may stop the video at 4:10 so that only the content on IP addresses is covered, as DNS will be covered later. In this case, you should split the video worksheet into two parts.
Discuss
You should review the material covered in the video.
The questions in the IP and DNS Video Worksheet (Optional) - Video Worksheet are a good place to start. The essential ideas and vocabulary students should know are:
- IP Address
- IP Packets
- IPv4 versus IPv6
Optional Quick activity: What's the IP address of the computer you're using right now?
There are a number of ways to figure out your IP address. An exploratory way is to do a web search for: *"What's my IP address?"
That will lead to finding something, but you should be cautioned that the answer isn't always simple.
For example, if you are in a computer lab and use a site like What's my IP Address? it's likely that all of the computers in the classroom will report the same address. This is because the computers in a computer lab are probably using the same shared connection and might look to the outside world like they're all coming from the same place.
You can also look at a computer's settings to see what it thinks it's IP address is.
Assessment
Questions (also on Code Studio):
-
To improve communication in playing Battleship on the Internet Simulator your group invented a(n):
a) heuristic
b) algorithm
c) protocol
d) encoding
-
Which of the following information is not necessary in your protocol to play Battleship?
a) cell number
b) from
c) to
d) time
-
Even with a good protocol, what are some privacy and security challenges while playing Battleship on the Internet Simulator?
Extended Learning
- Security and Privacy: If the messaging scheme your group designed was really used on the Internet, what could go wrong in terms of security and privacy? Think about what a malicious person could do. What if the messages sent weren't about a game but about something more personal like a conversation with a friend, or communicating with a bank?
- There are two major security problems with the current version:
- Anyone can fake a return address. Bob could send you a message and claim it’s “from Alice,” and you’d have no way to confirm who sent it.
- Everyone can view everyone else’s messages! Because all messages are “broadcast” over Internet Simulator, messages have no expectation of privacy.
- There are two major security problems with the current version:
- Lesson Vocabulary & Resources
- 1
Teaching Tip
Student Instructions
Unit 1: Lesson 9 - The Need for Addressing
Background
In this lesson we use the Internet Simulator to communicate with more than one person at a time. This introduces problems because without the right protocols it's hard to tell which message is meant for which person. In this lesson you will begin to investigate how a message is broadcast over a network and how we can ensure a message is delivered to the right person. It requires inventing some kind of addressing protocol, but careful, it's easy for messages to get clobbered!
Vocabulary
- IP Address - A number assigned to any item that is connected to the Internet.
- Packets - Small chunks of information that have been carefully formed from larger chunks of information.
- Protocol - A set of rules governing the exchange or transmission of data between devices.
Lesson
- Play Battleship unplugged
- Play Battleship using an Internet simulator
- Invent an communication system for use in the Battleship game
- Learn about the requirements of an internet addressing protocol
- Invent an efficient and flexible addressing protocol for the battleship game
Resources
- Internet Simulator: Broadcast
- Student Overview
- The Internet: IP Addresses & DNS
- Student Overview
Student Instructions
Describe the addressing system your group devised.
How did your group decide upon a system for sending messages in the Battleship simulator?
Were there disagreements or problems? How were they resolved?
Student Instructions
Even with a good protocol, what are some privacy and security challenges while playing battleship on the Internet Simulator?
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2011)
CD - Computers & Communication Devices
- CD.L2:6 - Describe the major components and functions of computer systems and networks.
- CD.L3A:9 - Describe how the Internet facilitates global communication.
CL - Collaboration
- CL.L2:3 - Collaborate with peers, experts and others using collaborative practices such as pair programming, working in project teams and participating in-group active learning activities.
Computer Science Principles
6.1 - The Internet is a network of autonomous systems.
6.1.1 - Explain the abstractions in the Internet and how the Internet functions. [P3]
- 6.1.1C - Devices and networks that make up the Internet are connected and communicate using addresses and protocols.
- 6.1.1D - The Internet and the systems built on it facilitate collaboration.
- 6.1.1F - The Internet is built on evolving standards, including those for addresses and names.
- 6.1.1H - The number of devices that could use an IP address has grown so fast that a new protocol (IPv6) has been established to handle routing of many more devices.
6.2 - Characteristics of the Internet influence the systems built on it.
6.2.1 - Explain characteristics of the Internet and the systems built on it. [P5]
- 6.2.1C - IP addresses are hierarchical.
6.2.2 - Explain how the characteristics of the Internet influence the systems built on it. [P4]
- 6.2.2D - Interfaces and protocols enable widespread use of the Internet.
6.3 - Cybersecurity is an important concern for the Internet and the systems built on it.
6.3.1 - Identify existing cybersecurity concerns and potential options to address these issues with the Internet and the systems built on it. [P1]
- 6.3.1A - The trust model of the Internet involves tradeoffs.
