Lesson 11: Packets and Making a Reliable Internet
Overview
In this lesson student develop a protocol for reliably sending a message over an unreliable internet. The Internet Simulator has been setup for this lesson to restrict messages to no more than 8 characters each, and messages get dropped messages with some probability on every hop.
Students are given time to experiment with the Internet Simulator and develop their own protocol, possibly testing or demonstrating their protocol to their peers. At the conclusion of the lesson, students watch a short video explaining how these challenges are addressed in the real world with TCP - the Transmission Control Protocol.
Purpose
This is a problem-solving lesson. On the real Internet packet sizes are limited, and transmission is unreliable. In this lesson we have setup the Internet simulator to restrict packet-size to be very small - 16-bits for the to and from addresses plus only 8 ASCII characters. Also, the Simulator drops packets pretty regularly. In a set of 10 messages it's very likely one or two will be dropped. You may need to justify these restrictions to students, acknowledging that, yes, this is a simulation, but these types of constraints are a very real problem on the Internet.
The problem students have to solve is how to use the 8-ASCII-characters-worth of data to include both a piece of message you're trying to send, as well as information about how many messages (packets) there are in the whole message, and which number this packet is.
Students should invent or at least appreciate the need for something like the Transmission Control Protocol TCP. TCP was designed to overcome the inherent unreliability of the Internet. A small but non-negligible percentage of packets are lost in transmission because of faults in the infrastructure of the Internet. In order to constrain the extent of these errors, larger messages are divided into many packets which are individually routed to their recipient. The receiving computer will send an acknowledgement confirming the receipt of that packet. If the sending computer does not receive an acknowledgement, it will resend the packet until all packets have been acknowledged.
Since packets may arrive out of order, additional data must be included to indicate the order in which the packets should be arranged. Thus, while individual packets cannot be guaranteed to arrive, eventually an entire message can be accurately reconstructed.
Agenda
Getting Started (5-20 mins)
Activity (35 mins)
Wrap-up (10 mins)
Assessment
Extended Learning
View on Code Studio
Objectives
Students will be able to:
- Explain why protocols are necessary to overcome the underlying unreliability of the Internet.
- Justify the need for acknowledgements and packet numbering in TCP.
- Develop a protocol for reliable communication on the Internet.
Preparation
- Review functionality of Internet Simulator with transmission failure
- Copies of the Activity Guide
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
- U1L11 - Teaching Tips & Tricks Video - Video (download)
- Packets Unplugged Activity - Teacher Guide
For the Students
- The Internet: Packets, Routing, and Reliability - Video (download)
- Packets and Making a Reliable Internet - Activity Guide
Vocabulary
- Packets - Small chunks of information that have been carefully formed from larger chunks of information.
- TCP - Transmission Control Protocol - provides reliable, ordered, and error-checked delivery of a stream of packets on the internet. TCP is tightly linked with IP and usually seen as TCP/IP in writing.
Teaching Guide
Getting Started (5-20 mins)
Discussion Goal
- Build on prior knowledge of the structure of the Internet to reflect on the unreliability of the Internet
- Introduce the use of packets
- Motivate the need for protocols to ensure reliability when sending messages across the Internet.
Prompt:
Your friend sent you a message on the Internet, but you never received it. Based on what you already know about routers and the physical Internet, list what reasons might explain this fact.
Discuss:
In groups or as a class, students should share their lists. Use this opportunity to review the layers of the Internet already covered and potential flaws that could lead to a message getting dropped. Some example points of discussion:
- Wires are cut
- Interference on a radio channel
- Router malfunctions or cannot keep up with traffic being directed to it
Teaching Tip
This is an unplugged activity that was invented by teachers over a few different teacher professional development workshops for this curriculum. We've included it here because it was effective at both highlighting some of the issues around packets as well as very nicely setting up the problem students need to solve with the internet simulator.
Optional Unplugged Activity (15 mins)
Teacher Guide for unplugged activity: Packets Unplugged Activity - Teacher Guide
Synopsis The activity simulates issues of packets traveling on the internet with a paper-passing activity:
- Students pass pieces of paper (post its?) with writing on them to another student in the class
- Students cannot move from their seat - they only pass to someone within reach
- Teacher might provide some “interference” by grabbing post-its in transit and delaying or destroying them.
Transitional Remarks
When we communicate on the Internet, we are not just sending short text messages as we did yesterday. We also use the Internet to exchange documents, videos, music, and scientific data, and these files can easily grow to enormous size.
All of this would not be a problem if the Internet were perfectly reliable, but in reality, errors sometimes occur. Wires can be cut, routers can be overwhelmed with traffic, and interference with electric or radio signals can cause messages to become corrupted. The response to this problem is to split large messages into smaller pieces of information called packets.
It turns out that splitting up a message into packets provides many benefits. If a faster route opens up halfway through transmitting a large file, it is easy to reroute later packets in the transmission through that route.
Splitting up a message into smaller chunks doesn’t solve all the problems of unreliability on the Internet. Packets can still be dropped or arrive out of order.
Today’s challenge is to develop a protocol to reliably send messages even though the network itself is unreliable.
Activity (35 mins)
Introduce: new version of Internet Simulator - packets and unreliability.
Teaching Tip
You might want to demonstrate these new features of the Internet Simulator while explaining them.
If you have the ability to project your screen you can demonstrate before having students connect by:
- Opening 2 windows and connect to the simulator as yourself - you will see your name appear twice
- Send messages to yourself (using one of the IP addresses)
- Open the router logs to show packets dropped.
Remarks
The version of the Internet Simulator we will be using today has been structured to simulate the unreliability of the Internet.
In particular you'll notice a few changes:
- You will only be allowed to send packets containing 8 characters of text!
- Anything larger than 8 characters will be cut off...
- However, you may construct multiple packets prior to sending them, by clicking "Add Packet", and then send them all with one click of the "Send" button.
- Every message has a small chance of being dropped on each “hop” it makes between routers.
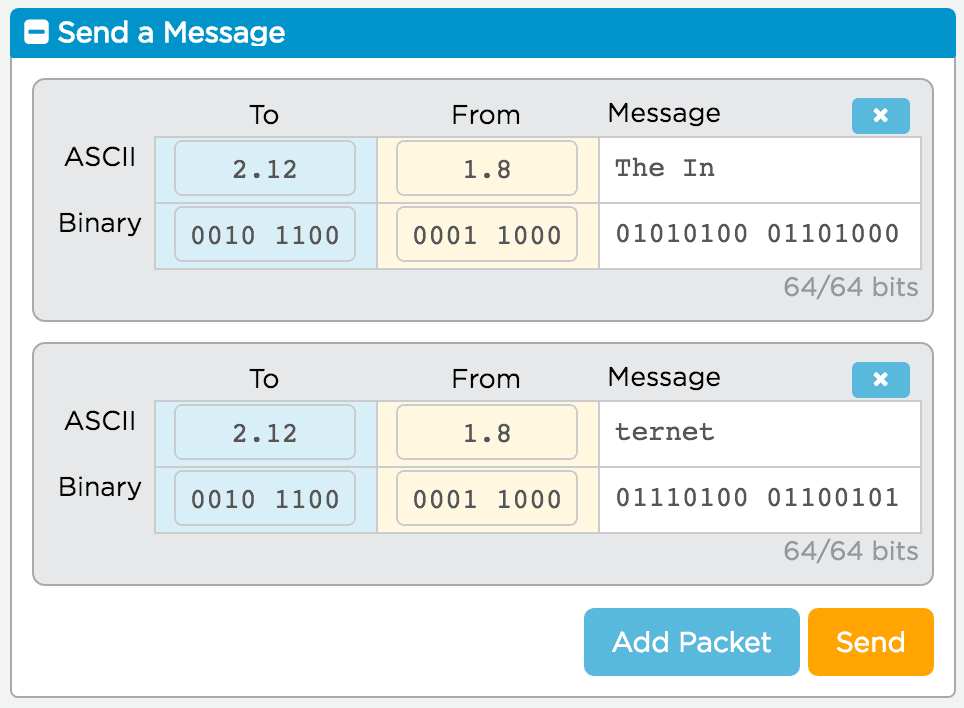
![]() Open Internet Simulator:
Open Internet Simulator:
Distribute the Activity Guide: Packets and Making a Reliable Internet - Activity Guide
- Place students in groups of 2 to 4 members.
- Students (individually or as a group, either is OK) should log into Code Studio and access the Internet Simulator.
- Add at least four routers (six or more is ideal; there’s no need to max out the connections on each router - it's fine if only one or two students are connected to a router)
- Have students join a DIFFERENT router from their groupmates.
Generate Traffic
- Students will need some time to get used to the changes introduced to the Internet Simulator.
- Provide them a couple minutes to exchange messages across routers.
- Make sure students try to construct a multi-packet message and send multiple packets at once to someone else
- Make sure they try the same thing for a classmate on ANOTHER router and then view the router logs to examine the result of these transmissions.
Teaching Tip
What to Look For
In student solutions, you should primarily be looking for:
- Some way to confirm receipt of a packet / message
- Some way to define the ordering of packets
This activity is designed to provide students a realistic encounter with the actual challenges of the Internet. It is OK if their solution does not perfectly match TCP, the actual solution to this problem.
The Focus
Should be on the protocol for the recipient to acknowledge or re-request missing packets. That is the real challenging part, and other parts of the protocol emenate from it. See: "The REAL problem to solve" below.
Suggested message format
To come up with a non-english message you could have students send a message as "ASCII" art. For example, you can treat the message as a grid and draw something with chacters. Here are two little examples: a letter "B" and a little character holding a torch.
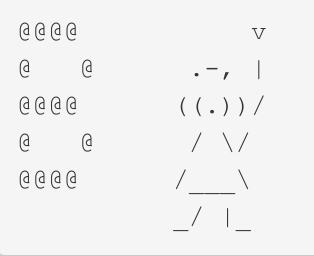
This is a clever way to send a drawing with ASCII text and students can come up with ways to break it up. The wider the drawing is, the more challenging the protocol will be to develop since each individual message is limited to only 8 characters.
Students should recognize:
- Packets are dropped with some frequency
- Packets of more than 8 characters are always truncated to just the first 8 characters
- Packets sometimes arrive out of order.
If students do not immediately recognize these points, draw them out in subsequent conversations.
Develop a Protocol
- Students will spend the rest of the class developing a protocol that will allow them to overcome the unreliability of the network so that a message can be sent and both sender and receiver can be confident the full message was received.
Content Corner
A Simple Solution
Sender: The simplest solution is to develop something akin to TCP, in which you use part of the message to indicate the the packet number and how many there are total. For example:
- Message 1:
14 Hi - Message 2:
24 Th - Message 3:
34 er - Meesage 4:
44 e!
Receiver: should know how many messages there are and can request a re-send of any that are missing. For example if you received messages 1, 2 and 4. You could send a message back, something like one of these:
req: 3 or need 3 or send 3
The way the real TCP works is this: every once in a while TCP sends back a "cumulative acknowledgement" of how many in-order packets it has received. For example, in an 8-packet message if you received packets:
1 2 _ 4 5 6 _ 8
Then you would send back a message like:
ack 2 or maybe ack 3
This would indicate to the sender that next packet you need is packet 3. The sender would send 3, and once you got it, your next message would be:
ack 6 or ack 7
Because you received packets 4, 5 and 6 already.
Guidelines for Protocol:
- All communication can only be done through the Internet Simulator.
- The full message sent will be at least 80 characters long - broken into at least 10 packets - and might be entirely random (i.e. there’s no way to use human intuition to reconstruct the message).
-
- The message is not known beforehand.
- Note: The Teaching Tips & Tricks video mentions a 20 character long message. 80 characters (10 packets) is the preferred length, as it results in more packets being dropped.
- The sender and receiver must be confident the full message was successfully transmitted and reconstructed.
The real Problem to Solve
The real problem to solve is to think about what the recipient of the messages should do to inform the sender of what’s missing and needs to be re-sent.
It’s tricky because any message the recipient sends back to the sender also stands a chance of being dropped or lost. Your protocol needs to overcome this unreliability for both the sender or receiver.
Provide students time to work on their protocol, iteratively testing their work and recording their final protocol in the space provided in the activity guide.
Test Protocols
- Provide students an opportunity to either present their protocols in written or visual form, or test them out by sending a randomly generated message of your choosing.
- The goal of this share-out would be to identify the main components of the protocols that groups developed in common.
Wrap-up (10 mins)
Video: The Internet: Packets, Routing, and Reliability
We’re going to watch a short video that talks a little more about the way this protocol and others help us ensure the reliability of the Internet.
Video: The Internet: Packets, Routing, and Reliability - Video
Connect activity to TCP
Either say these points or draw them out through discussion
- The challenges we encountered in today’s activity very closely mirror those that exist on the actual Internet.
- The response was the development of a protocol called the Transmission Control Protocol, or more simply, TCP.
- TCP divides larger messages into smaller packets which have ordering information added to their header.
- When a packet arrives at a destination computer, an acknowledgement is sent to the sender, letting them know they don’t need to resend that packet.
- Once all the packets have arrived, the ordering information in the headers of the packets allows them to be reordered to create the original message.
Assessment
Questions (also available on Code Studio):
-
Choose two: Pick the two statements about packets and routing on the Internet which are true.
a) Packets travelling across the Internet take a standardized amount of time and so can be counted on to arrive in the order they were sent.
b) TCP ensures messages can be reliably transmitted across the Internet.
c) TCP depends on the infrastructure of the Internet to be reliable enough to ensure no packets are lost in transmission.
d) TCP must account for the fact that packets may not arrive at a destination computer in the intended order.
-
Which of the following is NOT true about packets?
a) Packets are numbered, so if they arrive out of order, the message can be reassembled.
b) A message sent across the Internet can always be contained in a single packet.
c) Packets are routed on different paths from sender to receiver.
d) The receiver computer must confirm to the sending computer that each packet was received.
-
In your own words, what were the primary obstacles you needed to overcome in today’s challenge? How do these obstacles mirror actual problems encountered on the Internet?
Extended Learning
- There and Back Again: A Packet’s Journey and discuss questions that arise about how a packet travels from one person to another. (3:21)
- Easy Way to Understand Packets. Note: Headphones are recommended; this one has some dramatic music! (13:00)
- Protocols are developed by the Internet Engineering Task Force (among other groups), who publish Requests for Comment (or RFCs) detailing the components of the protocol. If students wish, they may have a look at the one of the actual RFCs for TCP here https://www.rfc-editor.org/rfc/rfc793.txt. RFCs exist for many of the protocols covered in this course.
- Blown to Bits (www.bitsbook.com), Appendix - The Internet as System and Spirit, pp. 301-309, “The Internet as a Communication System,” then answer the following question:
- It is interesting to think about the foresight (or luck?) that caused initial Internet designers to choose a packet-switched network as the basis for the Internet. What do you think, foresight or luck?
- Blown to Bits (www.bitsbook.com), Chapter 3 - Ghosts in the Machine, pp. 91-92, “Data Formats as Public Property,” then answer the following question:
- What do you think the Internet would be like today if different companies’ network protocols were still competing for adoption for the Internet, instead of TCP being the de facto standard?
- Lesson Vocabulary & Resources
- 1
Student Instructions
Unit 1: Lesson 11 - Packets and Making a Reliable Internet
Background
The internet is inherently unreliable. Wires can get cut, connections can get flooded with data, routers can crash. How can you ensure that a person receives the message you sent? In this lesson, we will investigate how packets and protocols to structure them can make the unreliable physical network appear to be reliable to people using it.
Vocabulary
- Packets: Small chunks of information that have been carefully formed from larger chunks of information.
- TCP: Transmission Control Protocol - provides reliable, ordered, and error-checked delivery of a stream of packets on the internet. TCP is tightly linked with IP and usually seen as TCP/IP in writing.
Lesson
- Explain why protocols are necessary to overcome the underlying unreliability of the Internet
- Develop a protocol for reliable communication on the Internet
- Justify the need for acknowledgements and packet numbering in TCP
Resources
- Internet Simulator: Packets
- Student Overview
Packets and Making a Reliable Internet
Challenge: Develop a protocol for reliably sending a message across an unreliable network
An Unreliable Internet Simulator: The current version of the Internet Simulator is modeled after some actual constraints of the Internet - Messages must be divided into packets which may contain at most eight (8) ASCII characters - Messages should be long enough to require at least 10 packets - Packets may not arrive in the order sent - Packets may be dropped while in transmission
Directions: In a group or individually join a router in the Internet Simulator and practice sending messages given these new constraints. Once you are comfortable with the challenge, iteratively design a protocol that can reliably send a message to a partner. You and your partner should join DIFFERENT routers.
Protocol Requirements: - All communication can only be done through the Internet Simulator - You must send a message that spans at least 10 packets (i.e. an 80 character ASCII message). - The protocol should account for the possibility that the characters might be entirely random (i.e. not necessarily English - do not count on human intuition to reconstruct the message. The message is not known beforehand.) - The sender and receiver must be confident the full message was successfully transmitted and reconstructed.
- The Internet: Packets, Routing, and Reliability
- Student Overview
Student Instructions
In your own words, what were the primary obstacles you needed to overcome in today’s challenge? How do these obstacles mirror actual problems encountered on the Internet?
Student Instructions
Teaching Tip
answer:
- B. A message sent across the Internet can always be contained in a single packet.
Student Instructions
Teaching Tip
Answers:
- protocol: A well-known set of rules and standards used to communicate
- packet: A chunk of information that gets sent on the internet
- Internet Protocol: The required structure of a packet to be sent on the internet
- IPv4 packet: A packet of data that uses 32-bit addresses
Student Instructions
(You may want to have seen the video: IP Addresses and DNS before responding to this)
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2011)
CD - Computers & Communication Devices
- CD.L3A:8 - Explain the basic components of computer networks (e.g., servers, file protection, routing, spoolers and queues, shared resources, and fault-tolerance).
- CD.L3A:9 - Describe how the Internet facilitates global communication.
- CD.L3B:4 - Describe the issues that impact network functionality (e.g., latency, bandwidth, firewalls, server capability).
CL - Collaboration
- CL.L2:3 - Collaborate with peers, experts and others using collaborative practices such as pair programming, working in project teams and participating in-group active learning activities.
Computer Science Principles
6.2 - Characteristics of the Internet influence the systems built on it.
6.2.1 - Explain characteristics of the Internet and the systems built on it. [P5]
- 6.2.1A - The Internet and the systems built on it are hierarchical and redundant.
- 6.2.1D - Routing on the Internet is fault tolerant and redundant.
6.2.2 - Explain how the characteristics of the Internet influence the systems built on it. [P4]
- 6.2.2A - Hierarchy and redundancy help systems scale.
- 6.2.2B - The redundancy of routing (i.e., more than one way to route data) between two points on the Internet increases the reliability of the Internet and helps it scale to more devices and more people.
- 6.2.2G - Standards for packets and routing include transmission control protocol/Internet protocol (TCP/IP).
