Lesson 6: The Cost of Free
Overview
This lesson focuses on the economic and consumer concerns around apps and websites that collect and track data about you in exchange for providing you a service free of cost. Often the quality of the service itself is dependent on having access to data about many people and their behavior. The main take-away of the lesson is that students should be more informed consumers of the technology around them. They should be able to explain some of the tradeoffs between maintaining personal privacy and using innovative software free of cost.
Purpose
Many consumers are unaware, or lack a sophisticated understanding, of how information about us is being collected and tracked by the technology we use every day. This issue goes beyond instances when data is stolen from companies or organizations we willingly provide it to. Instead, using computational tools, our movements through the physical and virtual world are being automatically tracked, stored, and analyzed. Cookies in our browsers keep a record of our movements on the Internet. Companies trade access to free tools and apps for the rights to track the data we upload to them. Advertisers develop personalized profiles of potential customers to better target advertising. Governments monitor traffic across the Internet at scales unimaginable without the use of computers. Yet we live in a world that increasingly relies on these digital tools, services and products. Most companies make great efforts to balance the tradeoffs between utility and privacy, but the issues can be tricky and raise confounding ethical dilemmas. We must now grapple with a question of just how much we value our privacy, and whether it is even possible to maintain in a digitized world.
Agenda
Getting Started (15 mins)
Activity 1 (30 mins)
Activity 2 (30 mins)
Wrap-up
Assessment
Extended Learning
View on Code Studio
Objectives
Students will be able to:
- Explain how and why personal data is exchanged for use of free software.
- Explain some of the privacy and economic tradeoffs involved in the collection and use of personal data.
- Describe the ways and reasons organizations collect information about individuals.
- Read and critically evaluate a data privacy policy.
Preparation
- Review the reading
- Review the teaching tips related to group work
- EXEMPLAR Privacy Policies
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Students
- Activity Guide - Privacy Policies - Activity Guide
- The Future of Big Data - Video
- WSJ article [original] - External Article
- WSJ article [annotated] - Article
- Cost of Free App
Teaching Guide
Getting Started (15 mins)
Video - The Future of Big Data
Opening Remarks
Yesterday we looked at ways that data we willingly give away could be lost and used to compromise our security.
What we often don’t think about, however, is just how much data is being collected about us without us even knowing it.
Especially as computers become ever more powerful and ubiquitous, it is becoming easier for vast amounts of data about us to be collected and for it to be used for a variety of purposes.
Video:
- The Future of Big Data - Video
- Video is also linked in Code Studio for Students
Transition:
The video mentions how your phone and websites you use track certain things about you. Today we’re going to find out a little bit more about it. Here are the primary questions we’re interested in:
- Why is this tracking necessary? What are the benefits and drawbacks?
- How can you find out what kind of data is tracked about you and by whom?
Thinking Prompt: What do you know about data collected about you every day?
Prompt:
- "Write down 2 or 3 websites, web services, or apps that you use the most or rely on the most to stay connected to friends and family, or use for “productivity” like school work."
Types of sites
Here is a list for you to help jog your students' memory. Encourage students to try to pick 2 or 3 different types, but also ones they've actually used.
- Education: Code.org, Khan Academy, Codecademy.com
- Social media: Facebook, Twitter, Instagram, Snapchat
- Online store: Amazon, Target, Walmart
- Search: Google, Bing
- Maps: MapQuest, Yahoo Maps, Google Maps
- Productivity: MS Office Online, Google Docs
- Mail & communication: Gmail, Hotmail, Yahoo Mail, Skype, Google Hangouts
- Streaming sites: Netflix, Spotify, Pandora
- Gaming sites: Steam, Xbox Live
- Banks and financial institutions: Chase, Citibank
- "For each website / service / app, fill in the following information - just what you know off the top of your head from your own experience or memory":
Info to write down for each site:
Students can just complete this in a journal or notebook. They should make a little table in order to compare side-by-side
- Name of Website / Service
- Do you have an account, or need to login?
- What kinds of data does (or could) this site potentially collect about you?
- Do you know if this data is shared with other people, companies or organizations? (If so, which ones?)
- Do you know how you would find out what data is collected or how it’s shared?
Give students about 5 minutes to write things down.
Quick Poll and Recap of Findings:
-
Show of hands: How many of the apps that you chose were free?
This will likely be all or almost all the apps.
-
Whip around: Name one piece of data the app you chose could potentially collect or know about you.
Try to get out as many different types as possible.
Transitional Remarks
- Wow, that’s a lot of data! If this stuff is “free,” but these companies make a lot of money, then it stands to reason that we are “paying” for these services with our data, because that’s the only thing we’re giving them in return for a service.
- What is the monetary value of your personal data?
- How is it used to make money? What are the tradeoffs? Let’s learn a little bit more.
Activity 1 (30 mins)
Part 1 - Reading: Wall Street Journal: Users Get as Much as They Give
Goal of Reading WSJ article
We want students to understand a bit about how collecting data is part of the business model for many apps / websites and that we often trade our personal data in order to get these services for free.
It’s slightly complicated by the fact that the services are overall better because of how many people use them while sharing data. But it does raise privacy concerns.
Teaching Tip
Individual reading
The full article is about 1200 words. It would probably take about 5-10 minutes for a person to read it. You could read quietly and then put students into small groups for the discussion.
Jigsaw We’ve prepared an annotated version that breaks up the article into 4 sections. It’s recommended that the reading be divided up three ways: Everyone should read the paragraphs denoted “Intro and Background” and then assign each of the remaining 3 sections to groups of students.
Use whatever jigsaw reading strategy you like so that students understand the key ideas of the reading.
Wall Street Journal: It’s Modern Trade: Web Users Get as Much as They Give
- Original article on wsj.com: WSJ article [original] - External Article
- Annotated/Jigsaw shorter version for jigsaw option: WSJ article [annotated] - Article
You can have students read individually or break it up to “jigsaw” it. Either option in the end will probably take the same amount of time. (See teaching tip for more info)
Discuss: Ask students in small groups to discuss what they learned from the reading and come up with a quick “temperature check”:
- "Right now, which way are you leaning? Too little privacy? Right amount?"
- "Are you willing to give up some privacy (and potentially some security) to have free access to modern innovative tools - do you trust companies to be good stewards of your data?"
- "Are you concerned? Do you think too much of your data is out of your control? Do you think too much personally identifiable data is given over to someone else?"
- "What other questions do you have?"
Notes for the discussion:
-
In the discussion, it’s worth noting the source of the article - The Wall Street Journal - and asking students to consider whether or not this information has a “pro-business” slant.
-
This is a very complex issue. The important thing is whether or not students are seeing both sides of the issue.
-
Try not to let students take the middle ground - “just the right amount of privacy” - as it’s an easy out. Press them to consider a specific case of one app or website and make a determination about that.
-
Caution: Try to keep the conversation focused on economic terms and the central question of “What is the cost of ‘free’?” It can be easy for this slip into a debate about privacy versus utility, in terms of government access to data, espionage, terrorism, etc. These are extremely important issues as well, but the conversation might get unwieldy. The focus of this lesson is about students becoming more informed consumers of the technology they use.
Activity 2 (30 mins)
Part 2 - Read a real data privacy policy
Goal of reading a privacy policy
We want students to see that it is possible to look up what data companies are collecting and who they share it with and why.
As an informed consumer, you should at least understand the issues well enough to make informed choices or take action.
Transitional Remarks
When you use most apps, websites, and social networks, they are collecting information about you in exchange for providing you a service, like connecting with your friends and sharing photos. Sometimes the service itself, like GPS, needs to track you just to be a useful app.
Other times, the data collected is useful to the company for making money.
Most of the companies that do track your data work hard to balance the tradeoffs between providing you with a service for free and the inherent risks such data collection poses to your personal privacy and security.
But what do they actually collect, and how do they use that data?
Let’s find out.
Most of these companies and organizations (the ethical ones) have a clear, well-written privacy policy. You’re going to pick one to investigate and report back.
Activity Guide - Privacy Policies
Distribute:
Prompt:
- "Pick one of the apps / websites that you chose at the beginning of class, and go find and read through that site’s privacy policy"
Here is a synopsis of what's in the activity guide for students to research.
- Students are asked to note what information the site says they collect, how they are using it, and (hopefully) how they are protecting it.
- The actual activity guide provides a bit more guidance for students about how to find answers to these questions.
-
Choose a Website and Find the Data Privacy Policy
-
What kinds of data are being collected? How many different kinds of data?
-
What service or feature is enabled by the data they are collecting? Why are they collecting it in the first place?
-
Who else is given access to that data? How are they using it?
-
Can you get access to your own data? Can you modify what is collected or used, or delete your data if you wish?
On a scale of 1-4, rate how comfortable you are with this company’s data policy? 1 - very uncomfortable 4-very comfortable
Discussion / Share out:
- Put students into groups of 3 to share what they found with each other.
-
Each group should report out 4 things for the policies reviewed in the group
- The names of the companies / organizations / websites reviewed by the group
- Notable similarities and differences in the kinds of data collected
- Just the number: How many privacy policies let you access, modify or delete your personal data?
- Just the number(s): How did you rate the policies on how comfortable you were?
-
Teacher should take note of the “comfort ratings.”
Prompt:
- "What’s your “temperature” on data collection now? Are you leaning toward more privacy? Or the same/less as there is now?"
Wrap-up
Where do you stand?
Prompt:
- "This lesson is entitled The Cost of ‘Free.’ What does that mean to you now?"
- "How would you explain The Cost of ‘Free’ to a family member, or person you just met, if you had only 60 seconds?"
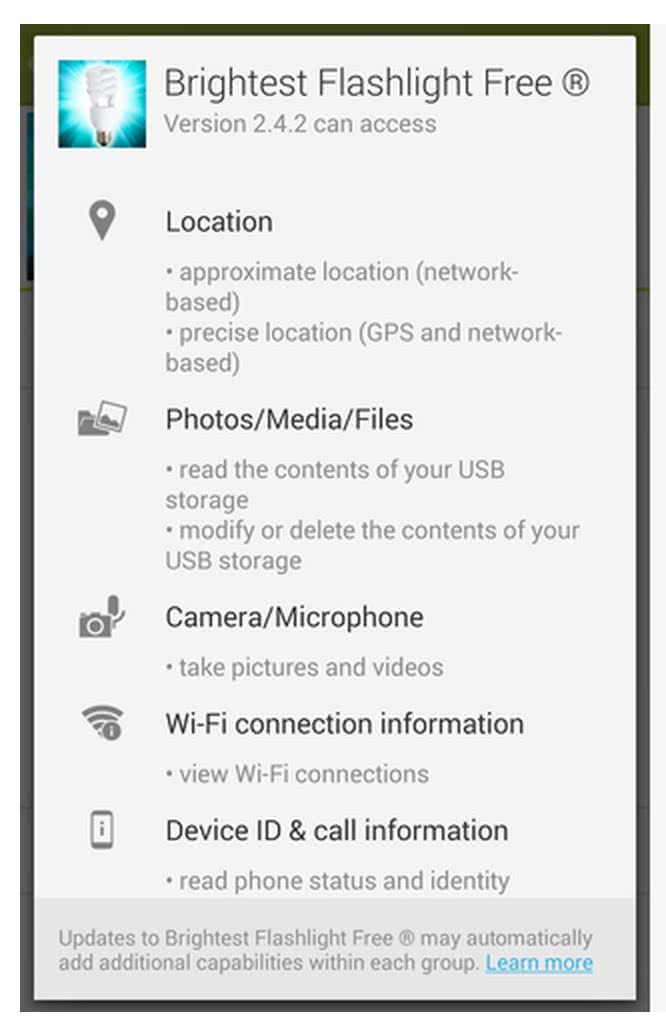
Would you install this “free app”?
As a final thought, what is your reaction to this app installation screen? (You can see a higher-resolution version in Code Studio.)
- What questions do you have?
- What would you want to know?
- What would you do to find that out?
- Bottom line: Would you install this app?
Assessment
- To get an idea of what to look for in the activity guides see the student exemplar in the teacher only area for Unit 4 lesson 4 here: EXEMPLAR - Activity Guide - Privacy Policies - Exemplar
Extended Learning
Articles in the news: You may choose to use the following articles to help deepen students' understanding of the pros and cons of the utility vs. privacy dilemmas that arise thanks to the massive amounts of data generated by modern technologies.
Share / Find Articles on the Forum: This list is provided as a starting point. We recommend you also check recent headlines for articles that are timely and pertinent. If you find a strong article we recommend you post a link in the forum for this lesson. We therefore also recommend you check the forum for articles your colleagues have shared.
Longer Reading
- Blown to Bits - Chapter 2 - Naked in the Sunlight: Privacy Lost, Privacy Abandoned
- Program or Be Programmed - Chapter 7: Social - Do Not Sell Your Friends
- Lesson Overview
- Teacher Overview
- Student Overview
Activity Guide EXEMPLAR: Privacy Policies
- AP Practice Response - Justify the Score
- Student Overview
AP Practice - Justify the Score
Written Prompt -- Here is a portion of the AP Explore Performance Task written response prompt 2d:
2d. Using specific details, describe
Sample Student Response -- here is a snippet of a sample student response addressing a data concern:
Zero -- based on the scoring guidelines listed below the student would NOT get a point for Row 6 and would likely NOT be awarded a point for Row 7 either.
Why? Here are the scoring guidelines for rows 6 and 7.

Justify the score
In the space provided below explain:
- Why the student would not be awarded either row based on the scoring guidelines.
- Make a suggestion(s) for how to modify the response so the student would get the point.
Teaching Tip
This one is potentially tricky because you have to use test-taking strategy to interpret the "LEAST TRUE" framing of the question. Laws about data collection and disclosure vary widely by country - the EU has a lot of laws required informed consent to collect data - and even varies by state in the US. But there is nothing that says a company is required to give you options.
Student Instructions
Student Instructions
AP Practice
The AP Explore Performance task requires you to provide short written responses about an innovation that you research. Here are portions of the prompts to consider:
-
Explain at least one beneficial effect and at least one harmful effect the computing innovation has had, or has the potential to have, on society, economy, or culture.
-
Using specific details, describe: at least one data storage concern, data privacy concern, or data security concern directly related to the computing innovation.
Respond to both of those prompts in light of what you learned about data privacy policies in this lesson. The "innovation" you choose could be narrow, like a specific app, or if it makes sense broad, like an entire company.
The main objectives of your response are to:
- Name one benefit (or potential benefit)
- Name one harmful effect (or potentially harmful)
- Be specific about the data that (presumably) leads to the harmful effect.
Limit your response to a few sentences for each point above.
Standards Alignment
View full course alignment
Computer Science Principles
3.3 - There are trade offs when representing information as digital data.
3.3.1 - Analyze how data representation, storage, security, and transmission of data involve computational manipulation of information. [P4]
- 3.3.1A - Digital data representations involve trade offs related to storage, security, and privacy concerns.
- 3.3.1B - Security concerns engender tradeoffs in storing and transmitting information.
- 3.3.1F - Security and privacy concerns arise with data containing personal information.
7.3 - Computing has a global affect -- both beneficial and harmful -- on people and society.
7.3.1 - Analyze the beneficial and harmful effects of computing. [P4]
- 7.3.1A - Innovations enabled by computing raise legal and ethical concerns.
- 7.3.1G - Privacy and security concerns arise in the development and use of computational systems and artifacts.
- 7.3.1H - Aggregation of information, such as geolocation, cookies, and browsing history, raises privacy and security concerns.
- 7.3.1J - Technology enables the collection, use, and exploitation of information about, by, and for individuals, groups, and institutions.
- 7.3.1K - People can have instant access to vast amounts of information online; accessing this information can enable the collection of both individual and aggregate data that can be used and collected.
- 7.3.1L - Commercial and governmental curation of information may be exploited if privacy and other protections are ignored.
- 7.3.1M - Targeted advertising is used to help individuals, but it can be misused at both individual and aggregate levels.
- 7.3.1N - Widespread access to digitized information raises questions about intellectual property.
CSTA K-12 Computer Science Standards (2017)
IC - Impacts of Computing
- 3A-IC-24 - Evaluate the ways computing impacts personal, ethical, social, economic, and cultural practices.
- 3A-IC-29 - Explain the privacy concerns related to the collection and generation of data through automated processes that may not be evident to users.
NI - Networks & the Internet
- 3A-NI-05 - Give examples to illustrate how sensitive data can be affected by malware and other attacks.
