Lesson 12: The Need for DNS
Overview
The core idea of this lesson occurs in the unplugged activity that kicks off the lesson, in which students try to keep track of IP addresses that had been randomly assigned to each student in the class, while at the same time the teacher occasionally changes students' addresses. This leads to identifying the need for an authoritative system for name-to-address mappings, known as the Domain Name System or DNS.
Students then briefly experiment with a DNS protocol in the Internet Simulator. The activity is similar, in that students will have to grapple with IP addresses changing in real time and use the built in DNS protocol to resolve the issues.
The lesson ends with students doing some rapid research about DNS and some of its vulnerabilities, particularly what are known as Denial of Service Attacks.
Purpose
The basic purpose of this lesson is to show students in kinesthetic and interactive ways some of the challenges solved, and created by, DNS. At its core, the DNS is "simply" a hierarchical system of computers and databases, that maps IP addresses to domain names. It enables Internet users to connect human-language locations on the Internet with numeric addresses used by IP. While distributed and hierarchical, it can be treated in the abstract as a centralized registry of locations on the Internet, allowing users to quickly find locations they are looking for and register themselves so that others may find them.
Agenda
Getting Started (15 mins)
Activity
Activity 2
Wrap-up
Assessment
Extended Learning
View on Code Studio
Objectives
Students will be able to:
- Give a high level description of DNS as a name-to-IP-address mapping system used on the Internet
- Give a few reasons why DNS is useful and necessary
- Describe at least one vulnerability of DNS and how an attack on it works
Preparation
- MUST print out and have prepared IP Address Labels for students walking into class
- Copies of Worksheet and Activity Guide
- Familiarize yourself with the Getting Started activity and what you need to do
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
- Unit 1 Lesson 12 - Teaching Tips & Tricks Video - Video (download)
- IP Address Labels - Teacher Resource
For the Students
- Names and Addresses - Worksheet
- DNS Partner Questionnaire - Activity Guide
- Research: DNS in the Real World - Activity Guide
- The Internet: IP Addresses and DNS - Video (download)
Vocabulary
- DNS - short for Domain Name System, this system translates domain names (like example.com) to IP addresses (like 93.184.216.34)
Teaching Guide
Getting Started (15 mins)
Teaching Tip
This Getting Started activity is a bit more involved than usual. It will probably take 10-15 minutes to complete and requires a lot of physical movement. The “Activity” portion of the lesson may be a little shorter than usual.
As students walk into class…
- Hand each student a single IP address (precut by teacher from IP Address Labels - Teacher Resource). Students should be instructed to hold onto their IP addresses, not share them, and await instructions.
- Make copies of Names and Addresses - Worksheet available -- each student will need one.
Content Corner
Background Info for the Activity
When computers talk to one another on the web, they don’t refer to each other by names; they use an IP address to indicate who they are and who they are sending a message to. Without this system, the packets would be impossible to route across the Internet. The problem with this system is that, while computers are fine with referring to other computers by numbers, humans are really terrible at remembering long strings of seemingly-random numbers. We’d prefer to identify a web page by its name, and besides, it makes remembering our favorite locations on the Internet (“Code.org” vs. 174.129.14.120) much easier!
DNS Unplugged
Instructions:
- When you walked in, I handed you a slip of paper with an IP address on it.
- You also should have a Names and Addresses - Worksheet worksheet.
- For the next 5 minutes, your goal is to complete an accurate list of IP addresses and names for all students in the room. You may only talk to one person at a time, but you may exchange as much information with that person as you want.
- GO!
Teaching Tip
Students may object that you’re making the task impossible. Part of the point of the exercise is that people’s IP addresses change all the time, and it’s difficult to keep track if no one, or no system, can be appealed to as an authority for name-to-address mappings.
You don’t need to linger with this activity, once you think students see what’s happening. Do enough to make the point and move onto the discussion.
Teacher Participation: As students are working, circulate quietly through the room.
Discussion
Discussion Goal
Students should understand that this is a realistic scenario -- IP addresses change all the time. This system of everybody-keep-track-of-your-own-list is highly inefficient. Every student is developing an identical list to one another. A central list would be better, and the Internet has a system for that.
- Prompt: Why did I keep taking your IP addresses?
- This simulates the fact that a computer’s IP address does not stay the same. For example, a person’s IP address on their phone changes quite frequently as they move around throughout their day and their phone tries to connect to the Internet from different locations.
- Prompt: Do you think the system we just simulated is an efficient way of collecting IP addresses? Are there any inefficiencies you observe? How could it be made better?
- A central list would be better, and the Internet has a system for that.
Activity
Teaching Tip
This is the first time with the Internet Simulator where students are communicating with a machine using a protocol, rather than with other human beings.
While students were able to fudge their protocols in the past, they will no longer be able to do so; it is essential that they use the exact protocol presented.
Transition to the Internet Simulator (see Code Studio):
- Direct students to the Internet Simulator and distribute DNS Partner Questionnaire - Activity Guide or direct students to the online document.
- Explain the new configuration of the simulator that includes a DNS server.
- A DNS server now appears attached to every router.
- We no longer can see anybody’s IP address. To get an IP address, we have “ask” the DNS server using a text-based protocol.
- Demonstrates how to send a request to the DNS for someone’s address. Let students try the DNS protocol to get the address of someone who is attached to their router.
- After a minute or two, get students’ attention to explain what will happen in the following activity.
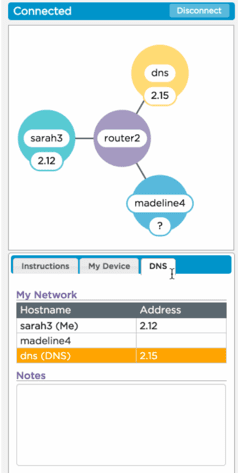
DNS in the Internet Simulator
(Explanation also in activity guide)
When you go to the Internet Simulator now, you will see a "DNS server" attached to the router. In order to communicate with someone else, you must first find their IP address by asking the DNS.
-
To begin, click over to the “DNS” tab to see all the hostnames of people on the router. You will see the address of the DNS (always 15) but will not see an address for anyone else on the router.
-
The DNS server responds to a text protocol that will give you someone’s IP address. The protocol is:
GET <hostnameOfPerson>
For example:
GET madeline4
- After the DNS has returned an IP address, you can type that IP address into the “To” field, enter a message, and then press “send.”
Directions:
(from the activity guide)
Content Corner
Especially in the world of mobile devices it is very common for a device to lose an IP address and need to re-acquire one - entering a tunnel, flying on a plane, even moving from one WiFi hotspot to the next.
It is true that at this point in time it's less likely that a web site with a registered domain name (like Code.org, google.com, or facebook.com) would rapidly change IP addresses, but the great thing about DNS is that even if they did, that change would be transparent to the public and you won't have to worry about it. Even so huge operations like Facebook, Twitter, etc. actually serve their sites on many hundreds (or thousands) of computers, all with different IP addresses - DNS helps manage that too, so you can just type Microsoft.com and it direct you to the right place.
As an analogy, think about a time when a friend or family member changed their phone number. That affects everyone who needs to know that number and causes some annoying problems. If we had a system like DNS for phone numbers, you'd never have to concern yourself with anything but remembering the person's name. Of course, every person on earth would have to have a unique name for this to work, so it's a bit impractical.
-
You are going to interview/have a conversation with a classmate using only the Internet Simulator. We’ve created a list of interview questions (on the next page) and you should both jot down each other’s responses.
-
To find the person, you will have to ask the DNS for her IP address. When you have retrieved the IP address, start the interview.
-
HOWEVER….As you’re working, if your teacher taps you and your partner, you both MUST disconnect and reconnect from the simulation. This is to simulate changing IP addresses.
-
Even though your IP address will change, your hostname will stay the same, so you’ll need to re-join a router and ask the DNS for your partner’s new IP address in order to continue having your conversation!
Teacher Participation:
As in the previous activity, you will “interfere” with the students’ activity by walking around the room and directing BOTH members of a pair to disconnect and reconnect.
When an IP address changes, there is no visual cue to anyone else on the Internet that the person they are talking to has moved.
Instead, they should send a request to the DNS to make sure that the IP address is correct every time they want to send a person a message.
Video: DNS

Remarks
You may remember (from the IP/DNS video that we saw several lessons ago) that you learned about the Internet system (v DNS) for sharing names and IP addresses. Let's watch that section again!
- Show the DNS portion of this video as a transition to the next activity.
- Video: IP and DNS - start at 4:10
Activity 2
Remarks
- Hopefully we all get the basic idea: the DNS is the large-scale system that translates human-readable web addresses into their numeric IP addresses so that computers can communicate.
- This system however was not designed to be secure and that has resulted in some major security incidents over time.
- You're now going to learn about some of them and how they work.
Rapid Research: DNS and DDoS attacks
Introduction:
Place students in groups of 4-6 people to complete their readings.
- Distribute: Research: DNS in the Real World - Activity Guide, one copy per student.
- Assign each group an article about DNS and DDoS attacks
- The list of articles can be found on the last page of the activity guide (consider not printing this page and distributing it digitally.)
- Students should complete the first page of the worksheet
Give students 15-20 minutes to read their article and make sense of the content.
- Groups should work together to complete their activity guide.
- Encourage groups to work together and make sure that at the end of the reading time, all students in the group feel comfortable with the technical content in the article.
Teaching Tips
Some articles are shorter than others and may not take the full 15 minutes to read. Consider giving these to students with lower reading levels or pairing them together so that a group reads two articles.
Jigsaw:
- Do a count-off to form new groups in which each member read a different article.
- Students should exchange information they learned with one another, recording the key points from each article in the space provided on the second page of the activity guide.
Wrap-up
What is DNS?
Discussion Goal
Some answers to the discussion questions:
- The Internet is basically a network of computers sending messages to request information and computers replying to messages to satisfy information requests. Computers need to identify “from” and “to” for all messages. Computers speak in numbers, not names.
- All communication online is via IP addresses. However, we are more familiar with human readable names, most notably URLs like “Code.org” or “Google.com.”
- We need a way to translate human-readable names into IP addresses.
- It is inefficient for everyone on the Internet to maintain a table of IP addresses.
- The DNS is NOT centralized, but it's not completely autonomous and distributed like routing, either. There is a hierarchical system of servers to maintain an authoritative table that, like a phone book, others can consult when they need to find an address.
- A properly functioning DNS system requires collaborative efforts among all users to ensure it is up to date and accurate.
Lead a discussion reviewing the IP and DNS systems.
Prompts: What is DNS?
- Why does the Internet use IP addresses?
- Why don’t we need to know IP addresses?
- Why do we need a Domain Name System?
- Why don’t we all maintain our own DNS?
- Is there one big DNS for the entire Internet?
- How do you think all these DNS servers are maintained?
Prompts: Security
- What is one vulnerability of DNS and how is that vulnerability attacked?
- What are the implications of an attack on a DNS server (or servers) - how does this affect your life?
Assessment
Code Studio: Assessment questions are available on the Code Studio.
Extended Learning
Dive Deeper on DNS: Check out this article with your students. It provides a deeper look into the DNS and what one sees when communicating with the DNS from the command prompt or terminal.
- Lesson Overview
- Student Overview
- Internet Simulator: DNS
- Student Overview
The Need for DNS
In this version of the Internet Simulator, a Domain Name System (DNS) is provided for you and knows the IP addresses of all connected computers. You can only see the hostnames of other connected computers.
The address of the DNS is always <yourRouterNumber>.15. Send a message with protocol GET [hostname], for example GET Bob2, to the DNS to get another student's address. You can keep track of the responses in the Notes section in the DNS tab.

- The Internet: IP Addresses & DNS_2019
- Student Overview
Teaching Tip
Answer:
- B. There are too few IP addresses to meet the current demand.
Student Instructions
Student Instructions
Why do computers need to periodically check the DNS for websites you have already visited?
Student Instructions
Why don’t we need to know the IP addresses for our favorite sites?
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2011)
CD - Computers & Communication Devices
- CD.L2:6 - Describe the major components and functions of computer systems and networks.
- CD.L3A:8 - Explain the basic components of computer networks (e.g., servers, file protection, routing, spoolers and queues, shared resources, and fault-tolerance).
- CD.L3A:9 - Describe how the Internet facilitates global communication.
- CD.L3B:4 - Describe the issues that impact network functionality (e.g., latency, bandwidth, firewalls, server capability).
CL - Collaboration
- CL.L2:3 - Collaborate with peers, experts and others using collaborative practices such as pair programming, working in project teams and participating in-group active learning activities.
Computer Science Principles
6.1 - The Internet is a network of autonomous systems.
6.1.1 - Explain the abstractions in the Internet and how the Internet functions. [P3]
- 6.1.1G - The domain name system (DNS) translates names to IP addresses.
6.2 - Characteristics of the Internet influence the systems built on it.
6.2.1 - Explain characteristics of the Internet and the systems built on it. [P5]
- 6.2.1B - The domain name syntax is hierarchical
6.2.2 - Explain how the characteristics of the Internet influence the systems built on it. [P4]
- 6.2.2C - Hierarchy in the DNS helps that system scale.
- 6.2.2D - Interfaces and protocols enable widespread use of the Internet.
CSTA K-12 Computer Science Standards (2017)
NI - Networks & the Internet
- 2-NI-04 - Model the role of protocols in transmitting data across networks and the Internet.
- 3A-NI-04 - Evaluate the scalability and reliability of networks, by describing the relationship between routers, switches, servers, topology, and addressing.
- 3A-NI-05 - Give examples to illustrate how sensitive data can be affected by malware and other attacks.
- 3A-NI-06 - Recommend security measures to address various scenarios based on factors such as efficiency, feasibility, and ethical impacts.
- 3A-NI-07 - Compare various security measures, considering tradeoffs between the usability and security of a computer system.
- 3B-NI-03 - Describe the issues that impact network functionality (e.g., bandwidth, load, delay, topology).

