Lesson 10: Routers and Redundancy
Overview
In this lesson students explore the benefits (and potential security concerns) associated with routing traffic across the Internet. Building on their introduction to IP addresses in the previous lesson, students use a version of the Internet Simulator that allows messages to be sent only to an intended recipient, as indicated by the IP address. The Internet Simulator also allows students to examine the traffic that goes through all of the (simulated) routers on the network. They will discover that messages go through many different routers, may not always take the same path to reach the final destination, and that the routers (and their owners) can see all of this traffic!
Purpose
The main purpose here is to use the Internet Simulator to dive into examining the network traffic that's generated by students in the class. Seeing traffic like this in real life is very hard if not impossible since only engineers of large networks have access to router data on a large scale, and it's also more complicated to understand. While our network is simulated and provides a simple view, the basics are the same, and quick investigations reveal interesting things. We want students to simply get a taste for both the scale and the implications of what routers do.
CS Background: A router is a computer designed to receive and redirect packets of information based upon the addressing information (e.g. an IP address) contained in the packet. Routers will either deliver a packet to its final destination or forward it to one of several other routers it is connected to. By monitoring current network conditions, a router can determine which of these will allow the packet to reach its destination fastest. There will often be redundant paths between two locations on the Internet, and so if one path is experiencing traffic or otherwise out of service, additional paths will be available. This redundancy makes the Internet more reliable and also helps the Internet to scale, accommodating new users (and routers!) as they are connected to the system.
Agenda
Getting Started
Activity
Wrap-up
Assessment
View on Code Studio
Objectives
Students will be able to:
- Describe the redundancy of routing between two points on the Internet.
- Evaluate the benefits and security concerns associated with the use of a routed system of sending packets.
- Send messages using a numeric addressing protocol with the Internet Simulator.
Preparation
- Review functionality of Internet Simulator with address fields as well as router / network tables
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Students
- Routers and Redundancy - Activity Guide
Vocabulary
- Network Redundancy - having multiple backups to ensure reliability during cases of high usage or failure
- Router - A type of computer that forwards data across a network
Teaching Guide
Getting Started
Discussion Goal
Goal: Prepare students to think about ways to overcome shortcomings of broadcasting messages (sending them to everyone on a shared line) through the use of routing. The prompt draws parallels between routing in the mail service and routing of traffic on the Internet.
Prompt: Imagine you were going to send a letter to a friend living in another state. List the steps you imagine your letter would have to take through the different parts of the postal system. Don’t worry if you’re not sure about your answers, just make an educated guess.
Teaching Tips
Keep it High Level: The exact details matter less than identifying multiple points where the letter is sorted and rerouted based on its intended destination. No need to go into great detail here, but the hope is to help students develop a mental model for how a system for routing messages looks and what role a router serves.
Discuss: Students can share their steps with a partner or group. Combine ideas from the class to create a single model of the steps involved, perhaps by writing / drawing it on the board. Draw attention to the number of times a person, post office, etc. must make decisions about where to send the letter next, i.e. "route" the letter.
- Example: Mailbox → Mail Carrier → Local Post Office → Regional Collection Center (of origin) → Regional Collection Center (of destination) → Local Post Office → Mail Carrier → Friend’s House
Transitional Remarks
When we send messages through a network we don’t actually want everyone on the network to receive them. If we include information about who the message is intended for then we can allow portions of the network to focus on sorting and routing messages, so that they can continue on their way to their intended target. In the mail system, mail facilities, post offices, or a mail carrier fills this role.
In a network of computers, certain computers called “routers” do the same thing, directing messages towards the target computer based on the IP addresses included in the message.
Activity
Introduce: New Version of the Internet Simulator - Routers
Remarks
Today's activity introduces the newest incarnation of the Internet Simulator
- Messages now have “To” and “From” addresses in a format similar to IP addresses (just an 8-bit address instead of a full 32 bits)
- This allows messages to be sent to a single intended recipient.
- The Internet Simulator also simulates the routing of messages across a network, with messages possibly being routed across multiple routers in unpredictable sequences before finally being delivered.
- This is done to simulate the way traffic travelling across the Internet is constantly rebalanced in response to over- or under-usage of some channels.
- A message will usually make it to its destination, but we can't know for sure how it will get there.
Choose a Router: Add a router if you need more space. Then join a router with a few of the people sitting closest to you. Ideally, you’ll have 3-4 classmates with you on your router.
Send a quick test message: Send a simple "hello" to a friend who is connected to the same router.
- Find friend's (small) IP address
- Send a message to that address
- Friend should send a response
Activity: Investigate Routed Traffic
Activity Goal
- have students become familiar with using an addressing protocol similar to IP
- highlight features of routed traffic on the actual Internet in an interactive way.
Ideally, students will recognize that:
- some messages may be dropped
- messages may take different paths to the same location
- routers can theoretically read all traffic moving across them.
Ask questions and direct investigations that help students encounter some of these surprising things.
Distribute Activity Guide: Routers and Redundancy - Activity Guide.
Teaching Tips
Big Picture: recognize that this activity is a repeated pattern of steps:
- Find a friend's IP address.
- Have a short conversation.
- Analyze the traffic using the "router logs" to learn something about the structure of the Internet and answer questions.
- First time: this is done with classmates on the same router.
- Second time: students communicate with classmates on a different router.
The format of the lesson lends itself to being completed as a class, rather than individually. The activity instructions here aim to help you structure the activity so that the class can move forward as a unit and explore the functionality of the tool together.
-
Students do not need to be in groups but it may help, especially early in the activity, if they are physically close to students who are connected to the same router as they are.
-
Lead students through the activity guide
-
Each of the following sections appears in the activity guide
- There are some notes for each of the sections, with suggestions for what you might do or say for each.
-
Lead students through the sections as you see fit.
Find a Classmate on Your Router: Ask students to join a router with some of their classmates, adding more if they need them. There should be at least three students on each router. Point out that messages now include a "To" and "From" IP address in their header. Ask students to use the network visualization to find the IP addresses of some of their classmates.
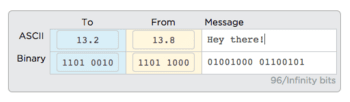
Have a Conversation: Ask students to conduct a short conversation (e.g. a simple greeting or a question and answer) with two friends on their router. They should verbally confirm that both sides are receiving their messages. Provide students a few minutes to practice. Help students construct their messages. If their To address is not constructed properly the message will be dropped.
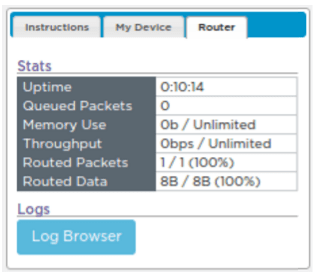
Read the Traffic: Once students have conducted their conversations, ask them to pause and demonstrate the ability to view router traffic in the Router tab. Students should use the data generated here to answer the first set of questions on the Activity Guide. Have students click the “Log Browser” button to view the table of router data.

Transitional Remarks
- Routing messages functions very differently from broadcasting.
- The messages are only sent to the user they are intended for.
- This is just like when you write a letter to a friend, where an address on the outside of the letter tells the mail service how to properly route your letter.
The Router Logs
- The view we have in this table of traffic wouldn't be available to a normal user on the network -- this is a simulation after all -- but it WOULD be visible to the router.
- A router needs to read the header of the message to route it correctly * But the contents of the message are right there too, and if it wanted, a router could read all the messages going across it, just like you did.
- This should raises some questions about privacy and security -- we'll talk more about this later.
Find a Classmate on a Different Router: The Internet Simulator can route messages between routers, allowing the entire class to communicate. Ask students to find two classmates on a different router and ask for their IP addresses. (They'll need to actually talk to one another; they currently won't be able to do it on the Internet Simulator.)
Have a Conversation: Again, students should conduct a short conversation with their two partners, confirming verbally that the messages are being received. Troubleshoot errors students may be encountering as before.
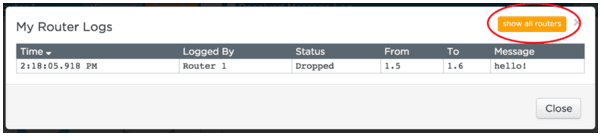
Reading Network Traffic: Once students have been able to talk with classmates, direct them again towards the "Log Browser" button. It is possible to read traffic across the entire network, not merely your router by clicking the “Show all routers” button. Ask students to open the network traffic and examine the traffic in order to answer the questions listed there.
Teaching Tips
Some of the behavior for the full-class Internet can be difficult to fully comprehend the first time. It may be a good idea to join a router and send a message to another router yourself, and then as a class, trace the path it takes hopping across multiple routers. If you send multiple messages with different contents, then you can see examples of a message taking different paths to the same location.
Explaining Redundancy: The simulations students used in today's lesson model many features of the actual Internet, most notably its redundant nature (there are many paths between locations). Assist students in identifying these features with the following comments, and note that at the top of the next page you’ll find a routing table that shows the different routes taken by the messages.
Remarks
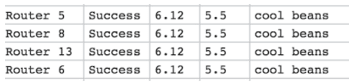
On the Internet Simulator we see messages appearing in the Router Logs multiple times (like in the image to the right). This is done to simulate a message passing through multiple routers on its way to its destination. A row is created each time it shows up at a new router.
-
Prompt: If you trace carefully you'll notice that messages between two people don't always visit the same routers along the way. This is not a mistake; it’s modeled after the way the actual Internet was designed. Why might the Internet have been designed to be flexible about how messages get from one person to another? Why go through the trouble of creating multiple paths between users?
- Efficiency: Communication lines can become backed up with traffic. The ability to choose whichever one currently has the least traffic improves the speed of transmission.
- Reliability: Having many redundant paths means if one goes down, there are many others that a message can take.
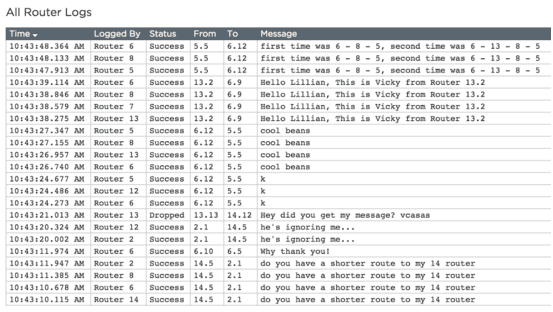
Teaching Tips
Here's a cheat sheet for the features of the Internet students saw today and how the Internet Simulator is simulating an actual feature of the Internet:
- To / From Address: Like an IP address, included on every message sent over the Internet.
- Dropped Messages: Poorly formed messages cannot be delivered and so are dropped, just like a letter with a bad address on it. Tomorrow you'll discuss more technical reasons messages are dropped.
- Multiple Hops: A message travelling across the Internet will visit many routers as each tries to forward it along the most efficient path to its destination.
- Different Paths: Routers respond to traffic on the Internet in real time. The best path at one moment might be backed up a few seconds later. Routers choose the current best path to get the message through.
Note: In the Internet Simulator the "hops" are chosen randomly. This is done to create multiple paths. Actual routers use algorithms to determine the best path to send a message along.
Wrap-up
Reflection: Ask students to answer the reflection questions at the bottom of this document: Routers and Redundancy - Activity Guide.
Discuss: Allow students to share their answers, either in groups or with the class. The discussion should touch on:
- Benefits of redundancy in a routed system, to provide many paths between users of the network.
- Routed messages aren’t seen by all users, but they can still be seen by owners of the router.
- If you control all the routers, you entirely control the way messages travel through the network, and additionally can see all the traffic.
Assessment
Code Studio: Assessment questions are available on the Code Studio.
- Lesson Overview
- Student Overview
- Internet Simulator: Routers
- Student Overview
An Updated Internet Simulator
Many changes have been made to the Internet Simulator.
Routers: Rather than being connected to your entire class you are now connected to a single router. You can see who else is on your router in the network diagram.

IP Addresses: Every user has a unique IP address. The first portion is the number of your router and the second is your own unique number. You can figure out the IP addresses of people on the router by looking at the network diagram.

Sending Messages: You can now send messages to a single other user. Fill in the "To" portion of the message with the IP address (including the period) of the person you'd like to send your message to.

Router Statistics: You can see useful information about the functioning of your router in the "Router" tab.

Router Logs: You can read a log of traffic both at the level of your router and the entire network by clicking the "Log Browser" button.

Teaching Tip
Answer:
- C: The first 4 bits of the address specify the router number that your friend is on
Student Instructions
Teaching Tip
Answers:
- B: The mail carrier would sometimes take different paths to deliver each letter to your home.
- C: Letters would be written on the outside of envelopes for all to read instead of being put inside envelopes.
Student Instructions
Teaching Tip
Answers:
- D: A packet travelling between two computers on the Internet may be rerouted many times along the way.
- E: A packet contains addressing information to allow routers to decide how best to forward along that packet towards its destination.
Student Instructions
Student Instructions
Describe the relative benefits of routing over a broadcast style of communication. Is routed traffic more secure than broadcasting? Justify your answer.
Student Instructions
Can you know in advance the path a message will take between you and another computer on the Internet? Justify your answer.
Standards Alignment
View full course alignment
CSTA K-12 Computer Science Standards (2011)
CD - Computers & Communication Devices
- CD.L3A:8 - Explain the basic components of computer networks (e.g., servers, file protection, routing, spoolers and queues, shared resources, and fault-tolerance).
- CD.L3A:9 - Describe how the Internet facilitates global communication.
- CD.L3B:4 - Describe the issues that impact network functionality (e.g., latency, bandwidth, firewalls, server capability).
CL - Collaboration
- CL.L2:3 - Collaborate with peers, experts and others using collaborative practices such as pair programming, working in project teams and participating in-group active learning activities.
Computer Science Principles
3.3 - There are trade offs when representing information as digital data.
3.3.1 - Analyze how data representation, storage, security, and transmission of data involve computational manipulation of information. [P4]
- 3.3.1A - Digital data representations involve trade offs related to storage, security, and privacy concerns.
- 3.3.1F - Security and privacy concerns arise with data containing personal information.
6.1 - The Internet is a network of autonomous systems.
6.1.1 - Explain the abstractions in the Internet and how the Internet functions. [P3]
- 6.1.1B - An end to end architecture facilitates connecting new devices and networks on the Internet.
- 6.1.1C - Devices and networks that make up the Internet are connected and communicate using addresses and protocols.
- 6.1.1E - Connecting new devices to the Internet is enabled by assignment of an Internet protocol (IP) address.
6.2 - Characteristics of the Internet influence the systems built on it.
6.2.1 - Explain characteristics of the Internet and the systems built on it. [P5]
- 6.2.1A - The Internet and the systems built on it are hierarchical and redundant.
- 6.2.1D - Routing on the Internet is fault tolerant and redundant.
6.2.2 - Explain how the characteristics of the Internet influence the systems built on it. [P4]
- 6.2.2B - The redundancy of routing (i.e., more than one way to route data) between two points on the Internet increases the reliability of the Internet and helps it scale to more devices and more people.
CSTA K-12 Computer Science Standards (2017)
NI - Networks & the Internet
- 2-NI-04 - Model the role of protocols in transmitting data across networks and the Internet.
- 3A-NI-04 - Evaluate the scalability and reliability of networks, by describing the relationship between routers, switches, servers, topology, and addressing.
- 3B-NI-03 - Describe the issues that impact network functionality (e.g., bandwidth, load, delay, topology).