Lesson 2: Explore PT: Make a Plan (1 hr)
Overview
This lesson uses the Explore PT Survival Guide - Student Guide as the backbone for a series of activities to ramp up to doing the actual Explore PT. It contains some brainstorming activities around what qualifies as a "computing innovation" for the task as well practical advice and strategies for handling some of the nuances of the task such as distinguising between a "harmful effect" and a "data security or privacy concern."
The lesson concludes by providing students with resources to make a plan to complete the task staring in the next lesson.
Purpose
These activities are designed to approach reviewing the Explore Performance Task in a whole-class-discussion inquiry-based way. It's not required that you do this, but there is a fair amount of reading to get through and this should help break it up.
Agenda
Getting Started (5 mins)
Activity (45-60 mins)
Wrap-up (10-15 Minutes)
View on Code Studio
Objectives
Students will be able to:
- Describe the elements and purpose of the Explore PT
- Describe the scoring guidelines for the Explore PT
- Evaluate sample Explore PTs by applying the scoring guidelines
Preparation
- Review the Explore PT Survival Guide - Student Guide
- Decide whether you are going to print the Explore PT Survival Guide - Student Guide - either in whole or in parts, or have students review and use the documents online.
- Reference the actual AP CSP Performance Task Directions for Students - Resource and Explore Performance Task - Scoring Guidelines 2018 - College Board Doc if necessary.
Links
Heads Up! Please make a copy of any documents you plan to share with students.
For the Teachers
For the Students
- Explore PT Planning Organizer - High Resolution PDF
- Explore PT Survival Guide - Student Guide
- AP CSP Performance Task Directions for Students - Resource
- Explore Performance Task - Scoring Guidelines 2018 - College Board Doc
Teaching Guide
Getting Started (5 mins)
Discussion Goal
Goal: The purpose of this discussion to warm up students' brains and recall the elements of the Explore PT. We want students to start thinking about choices in light of what they have to do for the Explore PT, rather than simply out of interest or "coolness." Hopefully, the two go hand in hand.
In particular we'll looking to drive home the point that your selection of a computing innovation should be done thoughtfully to make completing the task easier.
Prompt: Based on our review of the Explore PT yesterday...
- What are the main things you have to do for the Explore PT?
- What should you do first?
Discuss: Let students call out the things they remember. Make this a quick review just to remind them of what was covered in the previous lesson.
A few of the things you need to do:
- Make computational artifact
- Provide written responses to prompts
- Research
- Cite everything with sources.
What should you do first?
- Pick a good computing innovation!
Activity (45-60 mins)
Introduce The Explore PT Survival Guide
Remarks
Today we will use the Explore PT Survival Guide to get started with the Explore PT. The beginning of the packet has a number of quick activities that help get us in the right mindset for thinking about and doing the task so you are ready to hit the ground running.
The guide will be helpful to you through the entire process of completing the actual Explore Task as well.
Distribute: Explore PT Survival Guide - Student Guide
Read Overview (page 1): Have students read the Explore PT Overview section of page 1.
- The information about the task itself should not be news if you've already reviewed the Explore PT
- Focus on the suggested processs
Picking a Good Computing Innovation (3 mins)
Prompt: The Explore PT requires the selection of a computing innovation which includes a computer or program code (software) as an integral part of its functionality. Read the bottom of page 1: Picking a Good Computing Innovation. Based on what we learned yesterday looking at scored samples, and the criteria listed here, what are the characteristics of a computing innovation that make it a good choice for the Explore PT?
- Give students time to read
- Allow students to chat with a neighbor
- Highlight the 3 evaluation criteria for a computing innovation
- It is not necessary to do a whole group discussion here - this is just a kick off.
Transition: To get our brains moving we're going to look at a list of potential innovations or topics that someone might consider for the task.
Teaching Tip
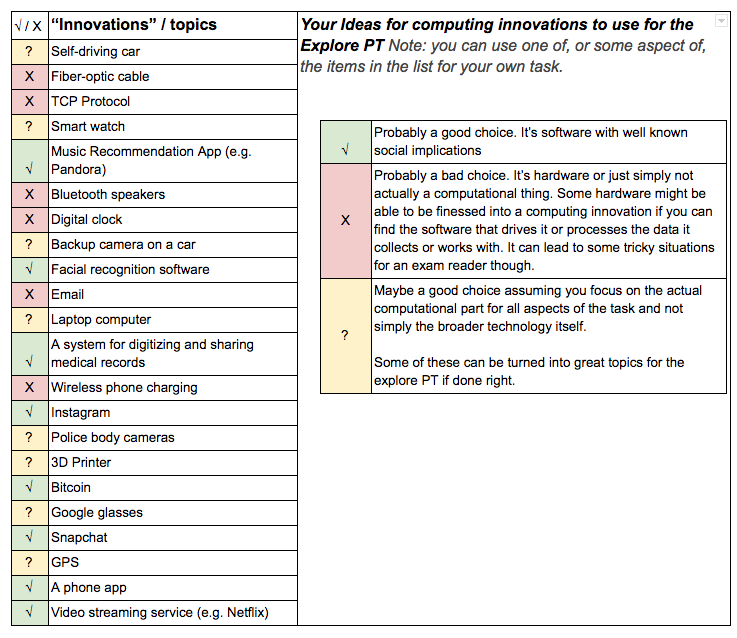 Click on the image at right to expand.
Click on the image at right to expand.
Strong Choices all involve computer code or computing as a core part of their functionality, have broad societal impacts, and make use of data.
Good Choices might need a little finessing to make sure you identify a computational aspect to report on.
Poor Choices either do not themselves include a computer or program code and so are not computing innovations.
Some of these are vague or are combinations of computing and non-computing innovations, which could prove challenging later in your project. For example "email" may be hard to research. Focusing in on a specific computing part of these innovations would help. For example: Police body cameras and 3D printers are a strong choice so long as you focus on the system that actually stores and processes data rather than the hardware.
Discussion Goal
Goal: The goal of this activity is NOT to come up with definitively correct or incorrect "answers" about the list of innovations. Many if not most technological innovations students come up with will be borderline cases that can be used for the Explore PT if framed the right way.
The purpose here is to spur disccusion about what makes for a computing innovation not lead to frustration about what the "right" answers are.
Computing Innovation Brainstorm Activity (10 mins)
Do the activity page 2 of the survival guide
- With your partner pick the "three best" and "three worst" potential Explore PT topics from this list.
- As you do so keep in mind that you're not picking your favorite topics, you're picking the ones that are best suited for completing the Explore PT.
- Also start to jot down ideas for things you want to research yourself.
Give students 5 minutes to look at the list of innovations and start to jot down their own ideas.
Discuss and Review Have students somehow share and compare their lists. Afterwards lead a discussion based on the patterns you see. You'll likely want to review the following points from the Survival Guide
- Not all technological innovations are computing innovations
- Focus or refine your choice so you're choosing the "computing" part of your innovation
- Keep the written responses in mind. If you already have some sense of the data your innovation uses (think literal binary data) and the impacts of the innovation on society you're probably on the right track.
Prompt: What other innovations did you think of while reviewing this list? Anything you'd be excited about researching?
- Allow students to call out a few of the ideas they had
- Encourage students to keep thinking about their own ideas for a computing innovation to use for the Explore PT as the go through the next activities.
Brainstorm: harmful effects v. data security concerns (10 mins)
Discussion Goal
Goal: 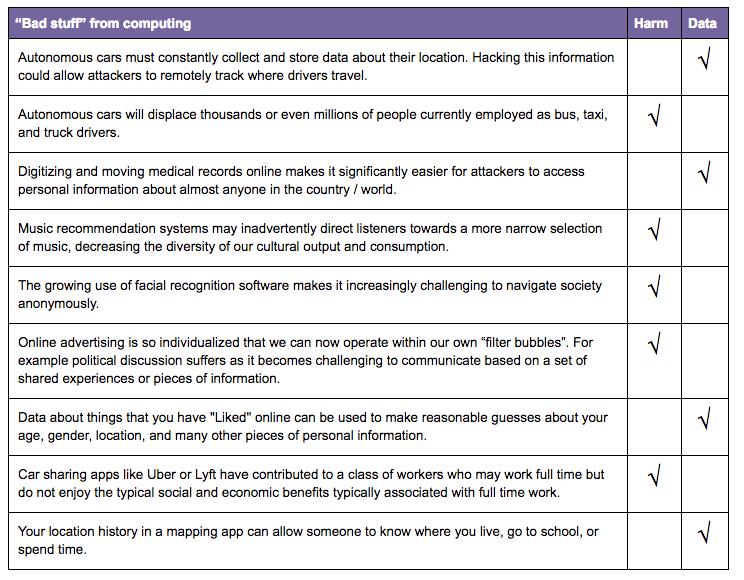 the goal here is gain clarity about the issue of the AP definition of a "harmful effect". Hopefully, the list of scenarios helps draw the distinction. Students should exit the conversation with more confidence that if during their research they learn about "bad stuff" related to a computing innovation that they can make the distinction between a harmful effect and a data concern as far as the PT is concerned. Click image at right to expand.
the goal here is gain clarity about the issue of the AP definition of a "harmful effect". Hopefully, the list of scenarios helps draw the distinction. Students should exit the conversation with more confidence that if during their research they learn about "bad stuff" related to a computing innovation that they can make the distinction between a harmful effect and a data concern as far as the PT is concerned. Click image at right to expand.
Do the activity page 2 of the survival guide
- Read the definitions at the top of the page.
- Look at the list of "bad stuff" resulting from computing innovations. Which ones are harmful effects (by the definition in the Explore Task) and which are data security concerns?
- With a partner go through and mark each as either a harmful effect or data security/privacy concern.
Discuss: Have groups compare answer sheets to see if there are any disagreements.
- Most of the "answers" follow the definitions closely, but a few are nuanced.
- It's a harmful effect if the "bad thing" affects a group of people resulting from the intended use of the innovation
- It's a data security/privacy concern if the data is being used in ways that weren't intended.
Rapid Research Activity - Harmful Effects (15 mins)
- Turn to Page 4 of the survival guide
- Read the instructions at the top of the page, and the notes at the bottom.
Discussion Goal
Goal: the biggest takeaway from this activity is that it can be very quick and easy to identify a harmful effect if using the right search terms and you can distinguish it from a data security/privacy concern. If it takes more than 10 minutes to find a harmful effect it's probably a sign you should pick a different computing innovation.
Prompt (activity instructions): now that you have a better sense of what "harmful effect" means you're going to see if you can find one for an innovation of your choosing. Pick one from the list of innovations earlier in the Survival Guide or one that you've thought of yourself, then go quickly look it up and see if you can fill in all the aspects of the table provided.
Discuss: What did you learn from doing rapid research? Is it easy or hard to find a harmful effect for a computing innovation.
- Have students compare with at least one other person in the class what they found.
- Partners should offer feedback about whether they think they've identified a "harmful effect" correctly.
- Highlight how quickly students were able to find articles about harmful effects. In a matter of minutes it's likely most students landed on something useable for the Explore PT.
Wrap-up (10-15 Minutes)
Making a plan
Discussion Goal
Goal: the goal here is to have students start planning in earnst for the Explore PT. Students should take seriously how they will allocate their time, and should think about how they probably want to maximize the amount of time they have to write the responses and create the artifact. Choosing an innovation and doing the initial research doesn't have to take very long.
- Turn to pages 5 and 6 of the survival guide
-
The pages are there to help you plan for doing your own Explore PT.
-
The Explore PT Planning Organizer is there as a place to take and categorize your notes and thoughts as you research your innovation.
- This Explore PT Planning Organizer - High Resolution PDF is a copy of what's on page 5 and is better for print if you want to print it.
-
The Explore PT Completion Timeline is there as a template for a daily guide for completing the PT.
Review pages 5 and 6 and add any initial notes or thoughts you have.
- Have students review the suggested timeline and make edits or updates to the schedule that will work for your school situation.
- NOTE the 8 hours is a minimum.
Prompt: taking into account all the activities we did today plus what you know about the Explore PT now, where do you expect you'll be spending most of your time? For which parts of the task should you maximize your time?
Give students a moment to think and share ideas with a partner.
Discuss: Have students share where they think most of their time should go.
- Probably want to maximize writing and artifact creation time
- Research can be done rapidly
- Don't forget to allocate time to proofread for easy-to-make mistakes that will cost points, like forgetting to cite sources.
Remarks
Now that we have methods and strategies for completing the task along with the beginnings of a plan, tomorrow we'll start the task in earnest.
- Explore PT - Make a Plan
- 1
Teaching Tip
Students can find all the links they need on this page. (If you are viewing this from within the lesson plan click Student Overview to see the student view of the page).
Please note: the Review and Planning documents are new resources for this lesson.
We've included links to college board documents from the previous lesson for reference so they don't have to go back and forth.
Student Instructions
Explore PT Prep - Making a Plan
Background
Make a plan to prioritize what you will do and when in order to complete the Explore PT in the allotted time.
Lesson
- Introduce The Explore PT Survival Guide
- Picking a Good Computing Innovation
- Computing Innovation Brainstorm Activity
- Harmful effects v. data security concerns
- Rapid Research - Harmful Effects
- Making a plan to complete the Explore PT
Resources
College Board Documents
- AP CSP Performance Task Directions for Students - College Board Student Handout
- Explore Performance Task - Scoring Guidelines 2018 - College Board Doc
Review and Planning Documents
- Explore PT Survival Guide - Student Guide (copy as MS Word, Google Doc)
- Explore PT Planning Organizer -- page 5 from survival guide - High Resolution PDF
Standards Alignment
View full course alignment
Computer Science Principles
1.1 - Creative development can be an essential process for creating computational artifacts.
1.1.1 - Apply a creative development process when creating computational artifacts. [P2]
- 1.1.1A - A creative process in the development of a computational artifact can include, but is not limited to, employing nontraditional, nonprescribed techniques; the use of novel combinations of artifacts, tools, and techniques; and the exploration of personal cu
- 1.1.1B - Creating computational artifacts employs an iterative and often exploratory process to translate ideas into tangible form.
1.2 - Computing enables people to use creative development processes to create computational artifacts for creative expression or to solve a problem.
1.2.1 - Create a computational artifact for creative expression. [P2]
- 1.2.1A - A computational artifact is anything created by a human using a computer and can be, but is not limited to, a program, an image, audio, video, a presentation, or a web page file.
- 1.2.1B - Creating computational artifacts requires understanding and using software tools and services.
- 1.2.1C - Computing tools and techniques are used to create computational artifacts and can include, but are not limited to, programming IDEs, spreadsheets, 3D printers, or text editors.
- 1.2.1D - A creatively developed computational artifact can be created by using nontraditional, nonprescribed computing techniques.
- 1.2.1E - Creative expressions in a computational artifact can reflect personal expressions of ideas or interests.
1.2.3 - Create a new computational artifact by combining or modifying existing artifacts. [P2]
- 1.2.3A - Creating computational artifacts can be done by combining and modifying existing artifacts or by creating new artifacts.
- 1.2.3B - Computation facilitates the creation and modification of computational artifacts with enhanced detail and precision.
- 1.2.3C - Combining or modifying existing artifacts can show personal expression of ideas.
7.5 - An investigative process is aided by effective organization and selection of resources. Appropriate technologies and tools facilitate the accessing of information and enable the ability to evaluate the credibility of sources.
7.5.1 - Access, manage, and attribute information using effective strategies. [P1]
- 7.5.1A - Online databases and libraries catalog and house secondary and some primary resources
- 7.5.1B - Advanced search tools, Boolean logic, and key words can refine the search focus and/or limit search results based on a variety of factors (e.g., peer-review status, type of publication)
- 7.5.1C - Plagiarism is a serious offense that occurs when a person presents another's ideas or words as his or her own. Plagiarism may be avoided by accurately acknowledging sources. 7.5.2 Evaluate online and print sources for appropriateness and credibility [P5]
7.5.2 - Evaluate online and print sources for appropriateness and credibility [P5]
- 7.5.2A - Determining the credibility of a soruce requires considering and evaluating the reputation and credentials of the author(s), publisher(s), site owner(s), and/or sponsor(s).
- 7.5.2B - Information from a source is considered relevant when it supports an appropriate claim or the purpose of the investigation
